新兴开源扫描器Golismero插件编写-TestingPlugin插件编写(二)
概述
Golismero是一款开源的Web扫描器,它不但自带不少的安全测试工具,而且还可导入分析市面流行的扫描工具的结果,比如Openvas,Wfuzz, SQLMap, DNS recon等,并自动分析。Golismero采用插件形式的框架结构,由纯python编写,并集成了许多开源的安全工具,可以运行在Windows,Linux, BSD,OS X等系统上,几乎没有系统依赖性,唯一的要求就是python的版本不低于2.7,其官网是:http://golismero-project.com 测试插件编写
TestingPlugin(测试插件)是进行安全检测的插件,而安全测试分为五个阶段:recon(侦查),scan(扫描),attack(攻击),intrude(入侵)和cleanup(扫尾)。这个五个阶段对应的测试插件存放位置如下表所示。 阶段:Recon(侦查) 位置:Plugins/testing/recon scan(扫描) Plugins/testing/scan attack(攻击) Plugins/testing/attack intrude(入侵) Plugins/testing/intrude cleanup(扫尾) Plugins/testing/cleanup 该五个阶段的测试插件是依次串行进行的,只有当前阶段的所有插件才会执行下一个阶段的插件,但是同一阶段的插件可以并行执行。测试插件的接口类如下所示:
| 接口类 | golismero.api.plugin.TestingPlugin |
| 基类 | + golismero.api.plugin._InformationPlugin+ golismero.api.plugin.Plugin +Object |
[Core] Name = Find Admin Page Module = findadminpage.py Class = FindAdminPage [Documentation] Description = Tries to find the admin page: www.jike521.com/admin Author = Jekkay Hu Version = 0.1 Website = http://www.freebuf.com Copyright = Copyright (C) 2011-2013 GoLismero Project License = GNU Public License然后再新建在plugins/testing/scan/findadminpage.py,代码如下:
#!/usr/bin/env python
# -*- coding: utf-8 -*-
from golismero.api.data.resource.url import Url
from golismero.api.data.vulnerability.suspicious.url import SuspiciousURL
from golismero.api.logger import Logger
from golismero.api.plugin import TestingPlugin
__license__ = """
please visit follwong website for more information
http://www.freebuf.com/
"""
class FindAdminPage(TestingPlugin):
"""
Find the admin page of website
"""
#----------------------------------------------------------------------
def __init__(self):
"""Constructor"""
self._keywordlist=set(['admin.html','administrator.html'])
self._count = 0
#----------------------------------------------------------------------
def get_accepted_info(self):
return [Url]
#----------------------------------------------------------------------
def recv_info(self, info):
"""process URL here"""
if not info or type(info) is not Url:
return
""""Tell controller """
#self.update_status(progress = None)
results=[]
# Test whether can get amount of urls[ answer is NO]
self._count += 1
try:
urlinfo=info.url.split("/")
findkey = self._keywordlist.intersection(set(urlinfo))
Logger.log_verbose("Testing %s..." %str(info.url))
if len(findkey) > 0:
# find the admin web page
# Report the vulnerabilities.
des = "Find the admin webpage [%s] " % str(info.url)
results.append(SuspiciousURL(
url = info,
substring = "no args",
level = "informational", # TODO: use the OSVDB API
description = des))
Logger.log_verbose(des)
except:
pass
return results
启动golismero来测试findadminpage插件,输入下列指令:
python golismero.py www.jike521.com -e findadminpage -e spider -o result.html -r inf其中-e spider表示启动爬虫插件,如果没有启动该插件就无法扫描到站点中的所有页面,输出的结果如下所示:
/----------------------------------------------\ | GoLismero 2.0.0b1 - The Web Knife | | Contact: golismero.project<@>gmail.com | | | | Daniel Garcia Garcia a.k.a cr0hn (@ggdaniel) | | Mario Vilas (@Mario_Vilas) | \----------------------------------------------/ GoLismero started at 2013-09-17 16:42:50.083000 [*] GoLismero: Audit name: golismero-lkQl6jgv [*] GoLismero: Audit database: golismero-lkQl6jgv.db [*] GoLismero: Added 4 new targets to the database. [*] GoLismero: Launching tests... [*] Web Spider: Started. [*] Web Spider: Spidering URL: 'http://www.jike521.com/' [*] Web Spider: Found 21 links in URL: http://www.jike521.com/ [*] Web Spider: Started. … [*] Find Admin Page: Started. [*] Find Admin Page: Working... [*] Find Admin Page: Find Admin Page: http://www.jike521.com/ [*] Find Admin Page: Finished. [*] Find Admin Page: Working... [*] Find Admin Page: Find Admin Page: http://www.jike521.com/img/tab.js [*] Find Admin Page: Finished. [*] Find Admin Page: Find Admin Page: http://www.jike521.com/admin.html <!> Vulnerability 'generic' dicovered by plugin 'Find Admin Page'. Risk level: 0 [*] Find Admin Page: Finished. [*] Find Admin Page: Working... …然后我们打开 result.html: 里面就有FindAdminPage插件所查找出来的漏洞信息。 插件调试
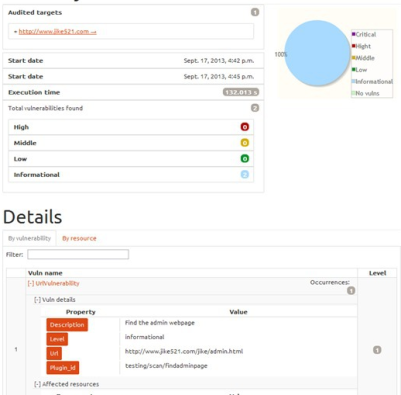
如果每次都启动golismero来测试插件,调试将灰常灰常麻烦,一是多进程调试非常麻烦,二是非常消耗时间,严重影响插件的开发效率,所以golismero里面提供了一个插件的测试脚本golismero/main/testing.py,我们可以直接简单地构建一个测试环境来测试脚本。比如,我们想调试一下FindAdminPage脚本,但不想通过启动glismero这个大工程,可以在在golismero的根目录下,创建一个测试脚本jekkay-test.py,内容如下:
#!/usr/bin/env python
# -*- coding: utf-8 -*-
import os
from os import path
import sys
script = __file__
if path.islink(script):
script = path.realpath(script)
here = path.split(path.abspath(script))[0]
if not here: # if it fails use cwd instead
here = path.abspath(os.getcwd())
thirdparty_libs = path.join(here, "thirdparty_libs")
if path.exists(thirdparty_libs):
has_here = here in sys.path
has_thirdparty_libs = thirdparty_libs in sys.path
if not (has_here and has_thirdparty_libs):
if has_here:
sys.path.remove(here)
if has_thirdparty_libs:
sys.path.remove(thirdparty_libs)
if __name__ == "__main__":
# As a portable script: use our versions always
sys.path.insert(0, thirdparty_libs)
sys.path.insert(0, here)
else:
# When installing: prefer system version to ours
sys.path.insert(0, here)
sys.path.append(thirdparty_libs)
from golismero.main.testing import PluginTester
from golismero.api.data.resource.url import Url
def main():
with PluginTester() as t:
u = Url("http://www.example.com/admin")
print t.run_plugin("testing/scan/findadminpage", u)
if __name__ =='__main__':
main()
值得注意的话,域名默认是www.example.com,假如需要修改域名的话,那么就需要更改成下面的代码:
with PluginTester(autoinit=False) as t:
t.audit_config.targets = ["http://www.mydomain.com/"]
t.init_environment()
u = BaseUrl("http://www. mydomain.com/")
print t.run_plugin("testing/recon/robots", u)
基本测试没有问题之后,然后再启动golismero进行测试。
相关阅读:
新兴开源扫描器Golismero插件编写-UI插件编写
by jekkay@freebuf
关注公众号:拾黑(shiheibook)了解更多
[广告]赞助链接:
四季很好,只要有你,文娱排行榜:https://www.yaopaiming.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注网络尖刀微信公众号
关注网络尖刀微信公众号随时掌握互联网精彩
赞助链接
排名
热点
搜索指数
- 1 习近平同马克龙交流互动的经典瞬间 7903947
- 2 确认完最后一步 反诈民警蹲地上哭了 7808956
- 3 仅退款225个快递女子曾打造富婆人设 7713058
- 4 2025你的消费习惯“更新”了吗 7617873
- 5 荷兰大臣:没想到中方叫停芯片出口 7522691
- 6 日本友人捐侵华日军家信内容残忍 7426132
- 7 连霍高速发生交通事故 造成9死7伤 7333513
- 8 危险信号!俄数百辆保时捷突然被锁死 7239201
- 9 众擎T800人形机器人一脚踹倒自家CEO 7139925
- 10 中疾控流感防治七问七答 7044697







 冷鹰
冷鹰







