Real World CTF 4th trust_or_not
trust_or_not
信息收集
题目文件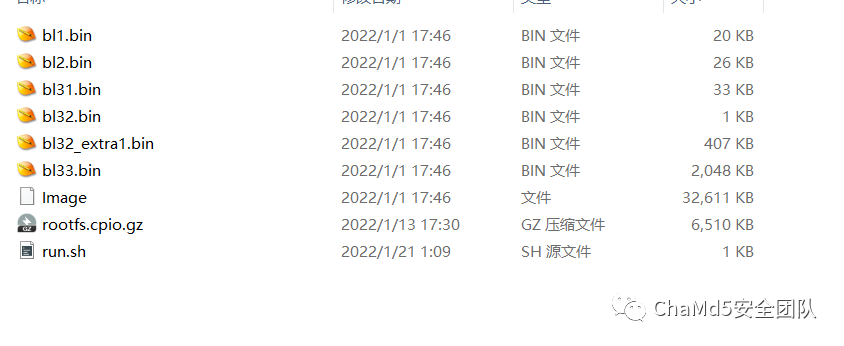 给出了6个bin文件,一个系统文件,一个启动脚本。这里通过对其名字进行搜索可以得到以下信息。
给出了6个bin文件,一个系统文件,一个启动脚本。这里通过对其名字进行搜索可以得到以下信息。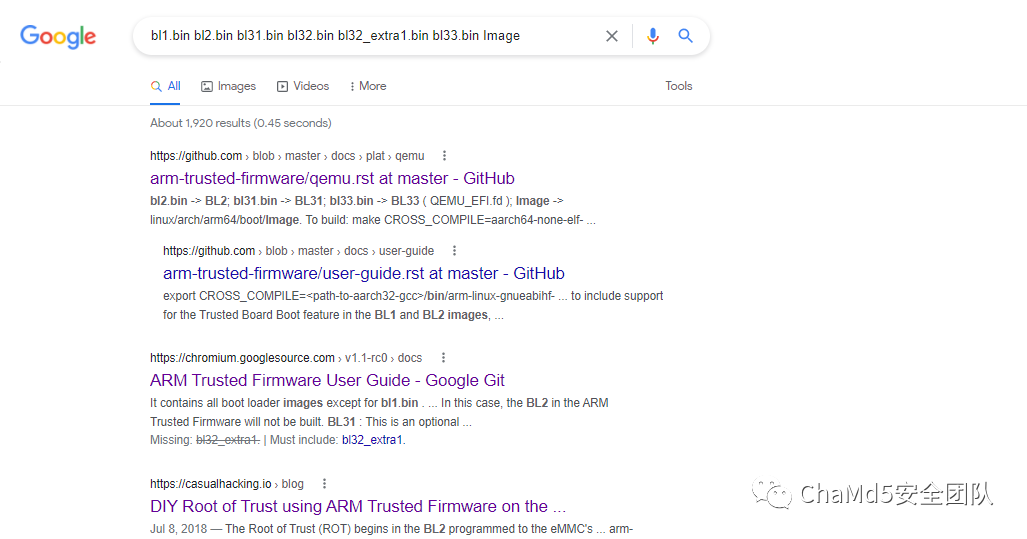 可以发现此处可能是一个OP-TEE内核,尝试对其
可以发现此处可能是一个OP-TEE内核,尝试对其binwalk解包。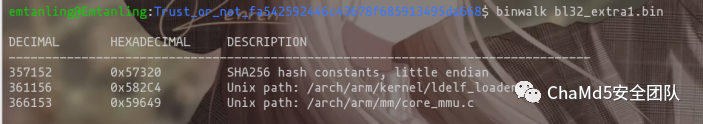
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
357152 0x57320 SHA256 hash constants, little endian
361156 0x582C4 Unix path: /arch/arm/kernel/ldelf_loader.c
366153 0x59649 Unix path: /arch/arm/mm/core_mmu.c
搜索文件可以确定为OP-TEE。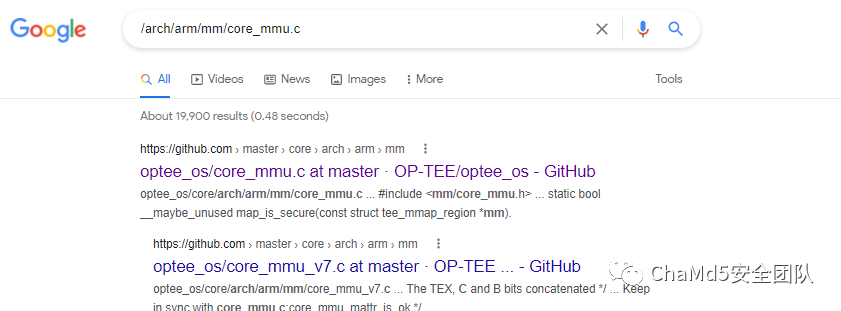 运行模拟此系统 查看
运行模拟此系统 查看rcS文件和inittab文件
# cat /etc/inittab
# /etc/inittab
#
# Copyright (C) 2001 Erik Andersen <andersen@codepoet.org>
#
# Note: BusyBox init doesn't support runlevels. The runlevels field is
# completely ignored by BusyBox init. If you want runlevels, use
# sysvinit.
#
# Format for each entry: <id>:<runlevels>:<action>:<process>
#
# id == tty to run on, or empty for /dev/console
# runlevels == ignored
# action == one of sysinit, respawn, askfirst, wait, and once
# process == program to run
# Startup the system
::sysinit:/bin/mount -t proc proc /proc
::sysinit:/bin/mount -o remount,rw /
::sysinit:/bin/mkdir -p /dev/pts /dev/shm
::sysinit:/bin/mount -a
::sysinit:/sbin/swapon -a
null::sysinit:/bin/ln -sf /proc/self/fd /dev/fd
null::sysinit:/bin/ln -sf /proc/self/fd/0 /dev/stdin
null::sysinit:/bin/ln -sf /proc/self/fd/1 /dev/stdout
null::sysinit:/bin/ln -sf /proc/self/fd/2 /dev/stderr
::sysinit:/bin/hostname -F /etc/hostname
# now run any rc scripts
::sysinit:/etc/init.d/rcS
# Put a getty on the serial port
ttyAMA0::respawn:/sbin/getty -L ttyAMA0 0 vt100 # GENERIC_SERIAL
# Stuff to do for the 3-finger salute
#::ctrlaltdel:/sbin/reboot
# Stuff to do before rebooting
::shutdown:/etc/init.d/rcK
::shutdown:/sbin/swapoff -a
::shutdown:/bin/umount -a -r
# cat /etc/init.d/rcS
#!/bin/sh
# Start all init scripts in /etc/init.d
# executing them in numerical order.
#
for i in /etc/init.d/S??* ;do
# Ignore dangling symlinks (if any).
[ ! -f "$i" ] && continue
case "$i" in
*.sh)
# Source shell script for speed.
(
trap - INT QUIT TSTP
set start
. $i
)
;;
*)
# No sh extension, so fork subprocess.
$i start
;;
esac
done
#
这里是对其配置,并没有发现开启什么服务。ps查看进程,也没有可疑进程。
# ps
PID USER COMMAND
1 root init
2 root [kthreadd]
3 root [rcu_gp]
4 root [rcu_par_gp]
5 root [kworker/0:0-mm_]
6 root [kworker/0:0H]
8 root [mm_percpu_wq]
9 root [rcu_tasks_kthre]
10 root [ksoftirqd/0]
11 root [rcu_preempt]
12 root [migration/0]
13 root [cpuhp/0]
14 root [cpuhp/1]
15 root [migration/1]
16 root [ksoftirqd/1]
18 root [kworker/1:0H-ev]
19 root [kdevtmpfs]
20 root [netns]
21 root [inet_frag_wq]
22 root [kworker/0:1-eve]
23 root [kworker/1:1-eve]
24 root [kauditd]
25 root [oom_reaper]
26 root [writeback]
27 root [kcompactd0]
28 root [ksmd]
29 root [khugepaged]
38 root [cryptd]
54 root [kintegrityd]
55 root [kblockd]
56 root [blkcg_punt_bio]
57 root [tpm_dev_wq]
58 root [ata_sff]
59 root [edac-poller]
60 root [devfreq_wq]
61 root [watchdogd]
62 root [kworker/1:1H]
63 root [rpciod]
64 root [kworker/u4:1-ev]
65 root [kworker/u5:0]
66 root [xprtiod]
67 root [kworker/u4:2-ev]
95 root [kswapd0]
96 root [nfsiod]
99 root [vfio-irqfd-clea]
100 root [kworker/1:2-mm_]
117 root /sbin/syslogd -n
121 root /sbin/klogd -n
144 tee /usr/sbin/tee-supplicant -d /dev/teepriv0
145 root [optee_bus_scan]
172 root udhcpc
173 root -sh
184 root ps
T神给了提示,查看OP-TEE源码。 此篇文章写明了加密流程。可以猜测
此篇文章写明了加密流程。可以猜测/data/tee/2文件是用op-tee加密。
解密流程
方法
之前文章中发现少了一个文件,即dirf.db文件。这里采用的办法是,使用官网给出的例子实现一个加密,之后进行替换,在进行解密。编译使用https://github.com/linaro-swg/optee_examples/tree/master/secure_storage文章中host目录下的程序,进行一次加密。
搭建环境
搭建工具链
# 下载
mkdir -p $HOME/toolchains
cd $HOME/toolchains
# Download 32bit toolchain
wget https://developer.arm.com/-/media/Files/downloads/gnu-a/8.2-2019.01/gcc-arm-8.2-2019.01-x86_64-arm-linux-gnueabi.tar.xz
mkdir aarch32
tar xf gcc-arm-8.2-2019.01-x86_64-arm-linux-gnueabi.tar.xz -C aarch32 --strip-components=1
# Download 64bit toolchain
wget https://developer.arm.com/-/media/Files/downloads/gnu-a/8.2-2019.01/gcc-arm-8.2-2019.01-x86_64-aarch64-linux-gnu.tar.xz
mkdir aarch64
tar xf gcc-arm-8.2-2019.01-x86_64-aarch64-linux-gnu.tar.xz -C aarch64 --strip-components=1
# 构建
cd $HOME
git clone https://github.com/OP-TEE/build.git
cd build
make -f toolchain.mk -j2
# 添加环境变量
export PATH=$PATH:$HOME/toolchains/aarch32/bin:$HOME/toolchains/aarch64/bin
构建optee_os
# clone
git clone https://github.com/OP-TEE/optee_os
cd optee_os
# build Armv7-A (AArch32)
make \
CFG_TEE_BENCHMARK=n \
CFG_TEE_CORE_LOG_LEVEL=3 \
CROSS_COMPILE=arm-linux-gnueabihf- \
CROSS_COMPILE_core=arm-linux-gnueabihf- \
CROSS_COMPILE_ta_arm32=arm-linux-gnueabihf- \
CROSS_COMPILE_ta_arm64=aarch64-linux-gnu- \
DEBUG=1 \
O=out/arm \
PLATFORM=vexpress-qemu_virt
# build Armv8-A (AArch64)
make \
CFG_ARM64_core=y \
CFG_TEE_BENCHMARK=n \
CFG_TEE_CORE_LOG_LEVEL=3 \
CROSS_COMPILE=aarch64-linux-gnu- \
CROSS_COMPILE_core=aarch64-linux-gnu- \
CROSS_COMPILE_ta_arm32=arm-linux-gnueabihf- \
CROSS_COMPILE_ta_arm64=aarch64-linux-gnu- \
DEBUG=1 \
O=out/arm \
PLATFORM=vexpress-qemu_armv8a
构建optee_client
# clone
git clone https://github.com/OP-TEE/optee_client
cd optee_client
# build 注:构建好的文件在/tmp/optee_client中
mkdir build
cd build
cmake -DCMAKE_C_COMPILER=arm-linux-gnueabihf-gcc -DCMAKE_INSTALL_PREFIX=/tmp/optee_client ..
make
make install
一些错误的解决办法 sudo apt install cmake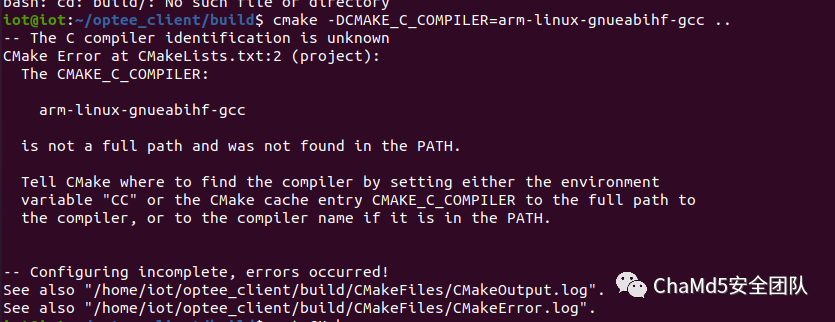
sudo apt install gcc-arm-linux-gnueabihf sudo apt-get install libc6-armhf-cross
构建optee_examples-master\secure_storage\host文件
make \
CROSS_COMPILE=arm-linux-gnueabihf- \
TEEC_EXPORT=/tmp/optee_client \
--no-builtin-variables
构建crack_optee-master
git clone https://github.com/qiuweixuan/crack_optee.git
make
注:需要将read_fs.cpp中的代码修改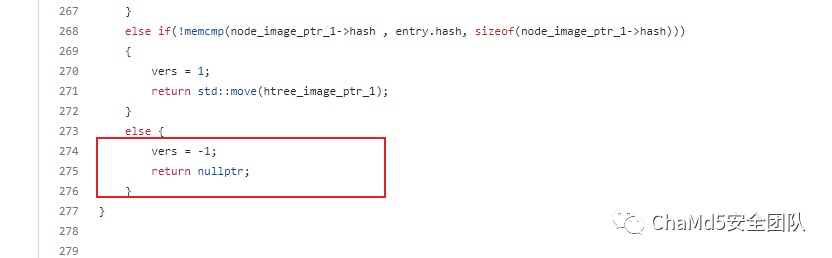 此处修改为
此处修改为
else if(!memcmp(node_image_ptr_1->hash , entry.hash, sizeof(node_image_ptr_1->hash)))
{
vers = 1;
return std::move(htree_image_ptr_1);
}
else {
vers = 1;
return std::move(htree_image_ptr_1);
}
flag
之后就很简单了,运行secure_storage\host\optee_example_secure_storage /data/tee。再运行 crack_optee 可以得到flag rwctf{b5f3a0b72861b4de41f854de0ea3da10}
补充
r3kapig的大佬们,写出了解密脚本,原文链接,膜拜。运行一下
参考链接
感谢T神的指点 https://www.codenong.com/cs106153863/ https://chromium.googlesource.com/chromiumos/third_party/arm-trusted-firmware/+/v1.1-rc0/docs/user-guide.md https://casualhacking.io/blog/2018/7/8/diy-root-of-trust-using-arm-trusted-firmware-on-the-96boards-hikey https://www.its404.com/article/jackone12347/121973662#TA_307 https://github.com/qiuweixuan/crack_optee/
end
招新小广告
ChaMd5 Venom 招收大佬入圈
新成立组IOT+工控+样本分析 长期招新
欢迎联系admin@chamd5.org

关注公众号:拾黑(shiheibook)了解更多
[广告]赞助链接:
四季很好,只要有你,文娱排行榜:https://www.yaopaiming.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注网络尖刀微信公众号
关注网络尖刀微信公众号随时掌握互联网精彩
- 1 中法友谊蕴山水 7904616
- 2 你以为的进口尖货 其实早已国产了 7808397
- 3 张荣恭:敢宣布“台独”大陆立刻动手 7712418
- 4 盘点2025大国重器新突破 7617706
- 5 部分银行上调存款利率 7522345
- 6 参军报国!全国征兵网上报名今日开始 7428281
- 7 美军承认:击落美军战机 7330429
- 8 尖叫之夜直播 7234403
- 9 大湾区大学正式成立 7135551
- 10 周末去哪玩?雪场“不打烊” 7045140







 Chamd5安全团队
Chamd5安全团队







