内存Fuzz与WINAFL实战
概述
FoxitReader


sxe ld:ConvertToPDF_x86
bm /a ConvertToPDF_x86!*
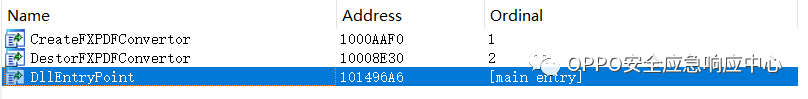
0:000> bm /a ConvertToPDF_x86!*1: 00000000`6d798e30 @!"ConvertToPDF_x86!DestorFXPDFConvertor"2: 00000000`6d79aaf0 @!"ConvertToPDF_x86!CreateFXPDFConvertor"0:000> gBreakpoint 2 hitConvertToPDF_x86!CreateFXPDFConvertor:6d79aaf0 a10cd1c36d mov eax,dword ptr [ConvertToPDF_x86!CreateFXPDFConvertor+0x4a261c (6dc3d10c)] ds:002b:6dc3d10c=00000000
_DWORD *CreateFXPDFConvertor(){_DWORD *result; // eaxvoid *obj; // eaxresult = dword_104AD10C;if ( dword_104AD10C )return result; // 调用malloc分配内存obj = alloc(0x1BDCu);if ( obj ){result = init_obj(obj); // 初始化对象dword_104AD10C = result;}else{result = 0;dword_104AD10C = 0;}return result;}
_DWORD *__thiscall init_obj(int this){int v1; // esiv1 = this;*this = &CFX_PDFConvertor::`vftable'; // 给对象设置虚表sub_1000A720((this + 4));*(v1 + 7104) = 0;*(v1 + 7108) = 0;*(v1 + 7112) = 0;*(v1 + 7120) = 0;*(v1 + 7116) = 1;dword_104AD104 = 0;*(v1 + 7124) = 0;*(v1 + 7128) = 0;return v1;}
.rdata:10336F1C ; const CFX_PDFConvertor::`vftable'.rdata:10336F1C ??_7CFX_PDFConvertor@@6B@ dd offset sub_1000B060.rdata:10336F1C ; DATA XREF: init_obj+6↑o.rdata:10336F1C ; sub_1000A8F0+BA↑o.rdata:10336F20 dd offset sub_10009B40.rdata:10336F24 dd offset sub_1000A2D0.rdata:10336F28 dd offset sub_1000A8F0
0:000:x86> lm m Conver*start end module name6d790000 6dcb5000 ConvertToPDF_x86 (export symbols) C:\Program Files (x86)\Foxit Software\Foxit Reader\Plugins\Creator\x86\ConvertToPDF_x86.dll0:000:x86> dd 0x6dac6f1c l4 // 查看虚表的函数的实际地址6dac6f1c 6d79b060 6d799b40 6d79a2d0 6d79a8f00:000:x86> bp 6d79b060 0:000:x86> bp 6d799b40 0:000:x86> bp 6d79a2d0 0:000:x86> bp 6d79a8f00:000:x86> bl0 e x86 6d79b060 0001 (0001) 0:**** ConvertToPDF_x86!CreateFXPDFConvertor+0x5701 e x86 6d798e30 0001 (0001) 0:**** ConvertToPDF_x86!DestorFXPDFConvertor2 e x86 6d79aaf0 0001 (0001) 0:**** ConvertToPDF_x86!CreateFXPDFConvertor3 e x86 6d799b40 0001 (0001) 0:**** ConvertToPDF_x86!DestorFXPDFConvertor+0xd104 e x86 6d79a2d0 0001 (0001) 0:**** ConvertToPDF_x86!DestorFXPDFConvertor+0x14a05 e x86 6d79a8f0 0001 (0001) 0:**** ConvertToPDF_x86!DestorFXPDFConvertor+0x1ac00:000:x86> gBreakpoint 3 hitConvertToPDF_x86!DestorFXPDFConvertor+0xd10:6d799b40 55 push ebp 0:000:x86> r // 首先调用6d799b40函数eax=6d799b40 ebx=0ad6a1a8 ecx=0ad6a1a8 edx=6dac6f1c esi=0088fb68 edi=00000002eip=6d799b40 esp=002cce0c ebp=002cece8 iopl=0 nv up ei pl zr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246ConvertToPDF_x86!DestorFXPDFConvertor+0xd10:6d799b40 55 push ebp0:000:x86> dps esp l4 # 参数为 2002cce0c 02398a54 FoxitReader!CryptUIWizExport+0x885514002cce10 00000002002cce14 711d4f33002cce18 02c2f814 FoxitReader!CryptUIWizExport+0x111c2d40:000:x86> gBreakpoint 4 hitConvertToPDF_x86!DestorFXPDFConvertor+0x14a0:6d79a2d0 55 push ebp0:000:x86> r // 然后调用6d79a2d0eax=002cec10 ebx=0ad6a10b ecx=0ad6a1a8 edx=6d79a2d0 esi=0ad6a1a8 edi=00000000eip=6d79a2d0 esp=002cce0c ebp=002cece8 iopl=0 nv up ei pl zr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246ConvertToPDF_x86!DestorFXPDFConvertor+0x14a0:6d79a2d0 55 push ebp0:000:x86> dps esp l6002cce0c 02398c22 FoxitReader!CryptUIWizExport+0x8856e2002cce10 002cec10002cce14 711d4f33002cce18 02c2f814 FoxitReader!CryptUIWizExport+0x111c2d4002cce1c 05d8149c002cce20 0088f9c00:000:x86> du 002cec10 # 参数是一个unicode字符串002cec10 "Foxit Reader PDF Printer"0:000:x86> gBreakpoint 0 hitConvertToPDF_x86!CreateFXPDFConvertor+0x570:6d79b060 55 push ebp0:000:x86> r # 调用 6d79b060eax=6dac6f1c ebx=0ad6a10b ecx=0ad6a1a8 edx=6d79b060 esi=0ad6a1a8 edi=00000000eip=6d79b060 esp=002cce04 ebp=002cece8 iopl=0 nv up ei pl zr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246ConvertToPDF_x86!CreateFXPDFConvertor+0x570:6d79b060 55 push ebp0:000:x86> dps esp l6002cce04 02398c3f FoxitReader!CryptUIWizExport+0x8856ff002cce08 002cce50002cce0c 00000000002cce10 00000000002cce14 711d4f33002cce18 02c2f814 FoxitReader!CryptUIWizExport+0x111c2d40:000:x86> du 002cce50 # 参数开头是被处理图片的地址002cce50 "C:\Users\XinSai\Desktop\honeyvie"002cce90 "w\5mb.jpg"0:000:x86> gBreakpoint 1 hitConvertToPDF_x86!DestorFXPDFConvertor:6d798e30 55 push ebp0:000:x86> r # 调用DestorFXPDFConvertor销毁创建的对象eax=00000000 ebx=0ad6a10b ecx=2156cf22 edx=0ad65078 esi=0ad6a1a8 edi=00000000eip=6d798e30 esp=002cce0c ebp=002cece8 iopl=0 nv up ei pl zr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246ConvertToPDF_x86!DestorFXPDFConvertor:6d798e30 55 push ebp0:000:x86> gBreakpoint 5 hitConvertToPDF_x86!DestorFXPDFConvertor+0x1ac0:6d79a8f0 a110d1c36d mov eax,dword ptr [ConvertToPDF_x86!CreateFXPDFConvertor+0x4a2620 (6dc3d110)] ds:002b:6dc3d110=0ad68e70sub_10009B4 参数为 this , 2sub_1000A2D0 参数为 "Foxit Reader PDF Printer" , unicode字符串sub_1000B060 参数为 this, 输入文件的全路径, 0, 0DestorFXPDFConvertor 函数会调用sub_1000A8F0去销毁对象
int main(){HMODULE hMod = LoadLibrary(_T("C:\\Program Files (x86)\\Foxit Software\\Foxit Reader\\plugins\\Creator\\x86\\ConvertToPDF_x86.dll"));if (hMod) {pCreateFXPDFConvertor = (CreateFXPDFConvertor)GetProcAddress(hMod, "CreateFXPDFConvertor");pDestorFXPDFConvertor = (DestorFXPDFConvertor)GetProcAddress(hMod, "DestorFXPDFConvertor");printf("CreateFXPDFConvertor:%p\n", pCreateFXPDFConvertor);char* obj = pCreateFXPDFConvertor();printf("create convertor:%p\n", obj);char* mod_base = (char*)hMod;vtable* vtb = (vtable*)(mod_base + 0x336f1c); // get vtable offsetprintf("module base:%p\n", mod_base);printf("vtb:%p\n", vtb);vtb->p_sub_10009B40(obj, 2);vtb->p_sub_1000A2D0(_T("Foxit Reader PDF Printer"));vtb->p_sub_1000B060(obj, (char*)_T("C:\\Users\\XinSai\\Desktop\\honeyview\\5mb.jpg"),0,0);pDestorFXPDFConvertor(obj);}return 0;}
0:000:x86> lm m Conver*start end module name6d790000 6dcb5000 ConvertToPDF_x86 (export symbols) C:\Program Files (x86)\Foxit Software\Foxit Reader\plugins\Creator\x86\ConvertToPDF_x86.dll0:000:x86> reax=00000000 ebx=00000000 ecx=00750070 edx=00000000 esi=0027ec60 edi=00278360eip=6d79995e esp=0022fa10 ebp=0022fa1c iopl=0 nv up ei pl zr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00010246ConvertToPDF_x86!DestorFXPDFConvertor+0xb2e:6d79995e 8b7910 mov edi,dword ptr [ecx+10h] ds:002b:00750080=????????0:000:x86> kb 4ChildEBP RetAddr Args to ChildWARNING: Stack unwind information not available. Following frames may be wrong.0022fa1c 6d79ac6b 00750070 00000000 ffffffff ConvertToPDF_x86!DestorFXPDFConvertor+0xb2e0022fa4c 6d79aed5 0027ec60 002776ec 002776e8 ConvertToPDF_x86!CreateFXPDFConvertor+0x17b0022fa68 6d79b0e6 00000000 a9d0a4e7 0022fbb4 # 在sub_1000B060里面0022faa4 013b67b6 00000000 00000000 00000000 ConvertToPDF_x86!CreateFXPDFConvertor+0x5f6
char *__thiscall crash_func(_DWORD *this, int invaild_address, unsigned int a3, unsigned int a4){obj = this;path_ = invaild_address;v6 = *(invaild_address + 16);// 解引 invaild_address+16 时异常
void __thiscall sub_1000ABA0(unsigned int *this, unsigned int a2){...............................................................if ( v8 ){v8[5] = 7;v8[4] = 0;*v8 = 0;crash_func(v8, a2, 0, 0xFFFFFFFF); // 调用发送crash的函数
char *__thiscall sub_1000AC90(char *this, int path_info){...............................................................p = *(path_info + 3188);if ( (*(path_info + 3192) - p) / 28 ){idx = 0;do{sub_1000ABA0(v3 + 797, p + idx); // 第二个参数为一个非法指针p = v2[797];++v29;idx += 28;}while ( v29 < (v2[798] - p) / 28 );}
signed int __thiscall sub_1000B060(const WCHAR *this, int path_info, int a3, char *a4){path_info_ = path_info;......................sub_1000AC90(this + 4, path_info_);
vtb->p_sub_1000B060(obj, (char*)_T("C:\\Users\\XinSai\\Desktop\\honeyview\\5mb.jpg"),0,0);
*(v3 + 936) = *(path_info + 3744); // 取结构体的字段*(v3 + 937) = *(path_info + 3748);*(v3 + 938) = *(path_info + 3752);*(v3 + 939) = *(path_info + 3756);*(v3 + 940) = *(path_info + 3760);*(v3 + 934) = *(path_info + 3736);p = *(path_info + 3188);if ( (*(path_info + 3192) - p) / 28 ){idx = 0;do{sub_1000ABA0(v3 + 797, p + idx); // 第二个参数为一个非法指针p = v2[797];++v29;idx += 28;}while ( v29 < (v2[798] - p) / 28 );}
0:000:x86> reax=003ece88 ebx=00000000 ecx=0a55a1ac edx=6d79b060 esi=0a55a1a8 edi=0a55a1aceip=6d79ac90 esp=003ece00 ebp=003ece38 iopl=0 nv up ei pl zr na pe nccs=0023 ss=002b ds=002b es=002b fs=0053 gs=002b efl=00000246ConvertToPDF_x86!CreateFXPDFConvertor+0x1a0:6d79ac90 55 push ebp0:000:x86> dd esp l2003ece00 6d79b0e6 003ece880:000:x86> db 003ece88003ece88 43 00 3a 00 5c 00 55 00-73 00 65 00 72 00 73 00 C.:.\.U.s.e.r.s.003ece98 5c 00 58 00 69 00 6e 00-53 00 61 00 69 00 5c 00 \.X.i.n.S.a.i.\.003ecea8 44 00 65 00 73 00 6b 00-74 00 6f 00 70 00 5c 00 D.e.s.k.t.o.p.\.003eceb8 68 00 6f 00 6e 00 65 00-79 00 76 00 69 00 65 00 h.o.n.e.y.v.i.e.003ecec8 77 00 5c 00 35 00 6d 00-62 00 2e 00 6a 00 70 00 w.\.5.m.b...j.p.003eced8 67 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 g...............003ecee8 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................003ecef8 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................0:000:x86> db 003ece88+0x208003ed090 43 00 3a 00 5c 00 55 00-73 00 65 00 72 00 73 00 C.:.\.U.s.e.r.s.003ed0a0 5c 00 58 00 69 00 6e 00-53 00 61 00 69 00 5c 00 \.X.i.n.S.a.i.\.003ed0b0 41 00 70 00 70 00 44 00-61 00 74 00 61 00 5c 00 A.p.p.D.a.t.a.\.003ed0c0 4c 00 6f 00 63 00 61 00-6c 00 5c 00 54 00 65 00 L.o.c.a.l.\.T.e.003ed0d0 6d 00 70 00 5c 00 31 00-35 00 37 00 33 00 30 00 m.p.\.1.5.7.3.0.003ed0e0 33 00 37 00 34 00 38 00-32 00 2e 00 70 00 64 00 3.7.4.8.2...p.d.003ed0f0 66 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 f...............003ed100 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................0:000:x86> db 003ece88+0x410003ed298 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................003ed2a8 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................0:000:x86> db 003ece88+0x618003ed4a0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................003ed4b0 00 00 00 00 00 00 00 00-00 00 00 00 00 00 00 00 ................0:000:x86> db 003ece88+0x820
0:000:x86> lm m Convert*start end module name6d790000 6dcb5000 ConvertToPDF_x86 (export symbols) C:\Program Files (x86)\Foxit Software\Foxit Reader\Plugins\Creator\x86\ConvertToPDF_x86.dll0:000:x86> kb 4ChildEBP RetAddr Args to ChildWARNING: Stack unwind information not available. Following frames may be wrong.003ecdfc 6d79b0e6 003ece88 c6266dd3 00000000 ConvertToPDF_x86!CreateFXPDFConvertor+0x1a0003ece38 02398c3f 00000000 00000000 00000000 ConvertToPDF_x86!CreateFXPDFConvertor+0x5f6003eed20 02396b76 082cad3c 08351664 00000000 FoxitReader!CryptUIWizExport+0x8856ff003eef74 023997e0 00adf9c0 082cad30 083087c0 FoxitReader!CryptUIWizExport+0x8836360:000:x86> lm m FoxitReaderstart end module name00f00000 03cd3000 FoxitReader (export symbols) C:\Program Files (x86)\Foxit Software\Foxit Reader\FoxitReader.exe
int __thiscall sub_1898690(_DWORD *this, int a2, int a3, int a4, int a5){char path_info[520]; // [esp+3Ch] [ebp-1E98h]char v83[2608]; // [esp+244h] [ebp-1C90h]int v84; // [esp+C74h] [ebp-1260h]int v85; // [esp+F00h] [ebp-FD4h]char v86[404]; // [esp+1A64h] [ebp-470h]char v87; // [esp+1BF8h] [ebp-2DCh]void *v88; // [esp+1DE0h] [ebp-F4h]int v89; // [esp+1DF0h] [ebp-E4h]unsigned int v90; // [esp+1DF4h] [ebp-E0h]__int16 v91[100]; // [esp+1DFCh] [ebp-D8h]int v92; // [esp+1ED0h] [ebp-4h]v81 = ((*v81)[2])(v81, v91);if ( !v81 )v81 = (**v65)(v65, path_info, 0, 0); // 调用sub_1000B060
00001E98 path_info db 520 dup(?)-00001C90 var_1C90 db 2608 dup(?)-00001260 var_1260 dd ?-0000125C db ? ; undefined-0000125B db ? ; undefined
int main(){HMODULE hMod = LoadLibrary(_T("C:\\Program Files (x86)\\Foxit Software\\Foxit Reader\\plugins\\Creator\\x86\\ConvertToPDF_x86.dll"));if (hMod) {pCreateFXPDFConvertor = (CreateFXPDFConvertor)GetProcAddress(hMod, "CreateFXPDFConvertor");pDestorFXPDFConvertor = (DestorFXPDFConvertor)GetProcAddress(hMod, "DestorFXPDFConvertor");printf("CreateFXPDFConvertor:%p\n", pCreateFXPDFConvertor);char* obj = pCreateFXPDFConvertor();printf("create convertor:%p\n", obj);char* mod_base = (char*)hMod;vtable* vtb = (vtable*)(mod_base + 0x336f1c); // get vtable offsetprintf("module base:%p\n", mod_base);printf("vtb:%p\n", vtb);vtb->p_sub_10009B40(obj, 2);vtb->p_sub_1000A2D0(_T("Foxit Reader PDF Printer"));unsigned int info_size = 0x2000;char* path_info = (char*)malloc(info_size);memset(path_info, 0, info_size);wchar_t* input_image = _T("C:\\Users\\XinSai\\Desktop\\honeyview\\5mb.jpg");wchar_t* output_pdf = _T("C:\\tmp.pdf");// 设置输入图片的路径wcscpy((wchar_t*)path_info, input_image);//设置输出图片的路径wcscpy((wchar_t*)(path_info + 0x208), output_pdf);printf("path info:%p\n", path_info);int ret = vtb->p_sub_1000B060(obj, path_info,0,0);printf("sub_1000B060 return: %d\n", ret);pDestorFXPDFConvertor(obj);free(path_info);}return 0;}
内存Fuzz
class MyClass{public:int __thiscall my_sub_1000B060(char* path_info, int a, int b) {char* input_image = "c:\\fuzz.jpg";wcscpy((wchar_t*)path_info, char_to_wchar(input_image));char* init_file = "c:\\init.jpg";INIT_SEED.buffer = read_file(init_file, &INIT_SEED.length);int ret = 0;while (true){fuzz(input_image); // 变异初始用例,并写入input_imageret = raw_sub_1000B060((char*)this, path_info, a, b); // 调用原始的目标函数debugger_printf("fuzzed function return:%d\n", ret);}}private:};int __stdcall DllMain(HINSTANCE hinstDLL, DWORD fdwReason, LPVOID lpReserved){char* base = NULL;unsigned long hook_func_addr = NULL;switch (fdwReason){case DLL_PROCESS_ATTACH://加载时候base = (char*)GetModuleHandle(_T("ConvertToPDF_x86.dll"));debugger_printf("base:%p\n", base);raw_sub_1000B060 = (sub_1000B060)(base + 0xB060);char buf[0x20];sprintf(buf, "%u", &MyClass::my_sub_1000B060);hook_func_addr = atoll(buf);if (Mhook_SetHook((PVOID*)&raw_sub_1000B060, (void *)hook_func_addr)) {debugger_printf("base: %p, func:%p", base, hook_func_addr);}break;default:break;}return TRUE;}
char buf[0x20];sprintf(buf, "%u", &MyClass::my_sub_1000B060);hook_func_addr = atoll(buf);



WinAFL
首先目标函数会打开一个文件读取数据,处理数据,最后会把文件关闭。
目标函数不会调用exit之类会结束进程的函数。
void fuzz_func(char* path) {vtb->p_sub_10009B40(obj, 2);vtb->p_sub_1000A2D0(_T("Foxit Reader PDF Printer"));memset(path_info, 0, 0x2000);wchar_t* input_image = _T("C:\\Users\\XinSai\\Desktop\\honeyview\\5mb.jpg");wchar_t* output_pdf = _T("C:\\tmp.pdf");wcscpy((wchar_t*)path_info, char_to_wchar(path));wcscpy((wchar_t*)(path_info + 0x208), output_pdf);int ret = vtb->p_sub_1000B060(obj, path_info, 0, 0);printf("sub_1000B060 return: %d\n", ret);}int main(int argc, char** argv){if (argc < 2) {printf("fuzz.exe path\n");return 1;}//加载dll到内存HMODULE hMod = LoadLibrary(_T("C:\\Program Files (x86)\\Foxit Software\\Foxit Reader\\plugins\\Creator\\x86\\ConvertToPDF_x86.dll"));if (hMod) {pCreateFXPDFConvertor = (CreateFXPDFConvertor)GetProcAddress(hMod, "CreateFXPDFConvertor");pDestorFXPDFConvertor = (DestorFXPDFConvertor)GetProcAddress(hMod, "DestorFXPDFConvertor");printf("CreateFXPDFConvertor:%p\n", pCreateFXPDFConvertor);// 创建好对象obj = pCreateFXPDFConvertor();printf("create convertor:%p\n", obj);//初始化全局虚表指针到DLL的虚表char* mod_base = (char*)hMod;vtb = (vtable*)(mod_base + 0x336f1c); // get vtable offsetprintf("module base:%p\n", mod_base);printf("vtb:%p\n", vtb);//调用函数处理数据fuzz_func(argv[1]);//释放分配的对象pDestorFXPDFConvertor(obj);}return 0;}
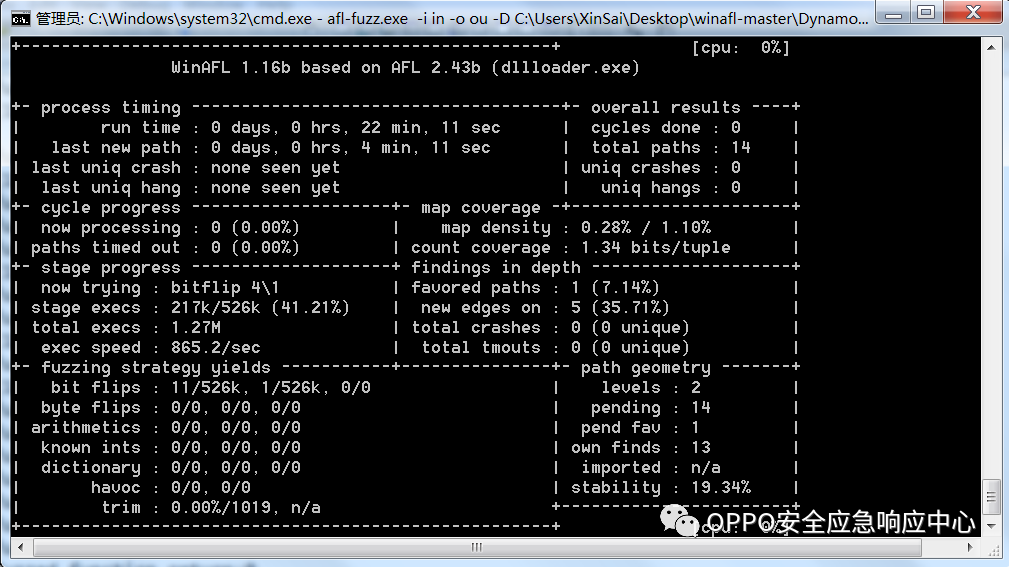
afl-fuzz.exe -i in -o out -D C:\Users\XinSai\Desktop\winafl-master\DynamoRIO-Windows-7.91.18187-0\bin32 -t 20000 -- -coverage_module ConvertToPDF.dll -fuzz_iterations 50000 -target_module dllloader.exe -target_method fuzz_func -nargs 1 -- C:\Users\XinSai\Desktop\foxitfuzz\dllloader\Debug\dllloader.exe @@
-D:指定dynamorio 的drrun.exe所在的路径-coverage_module:指定需要获取覆盖率的模块-target_method:目标函数的函数名,winafl会不断的执行该函数-nargs:target_method函数的参数个数-target_module:target_method所在的模块名-fuzz_iterations:指定target_method最多执行次数,达到次数后会重启程序
path\of\dynamorio\bin32\drrun.exe -c winafl.dll -debug -- C:\Users\XinSai\Desktop\foxitfuzz\dllloader\Debug\dllloader.exe c:\init.jpg
Module loaded, dllloader.exe........................................................Module loaded, ConvertToPDF.dll
IrfanView
"C:\Program Files (x86)\IrfanView\i_view32.exe" C:\example_2000.dwg

afl-fuzz.exe -i dwg -o dwgoutput -D C:\Users\XinSai\Desktop\winafl-master\DynamoRIO-Windows-7.91.18187-0\bin32 -t 20000 -- -coverage_module BabaCAD4Image.dll -fuzz_iterations 50000 -target_module BabaCAD4Image.dll -target_offset 0x1C20 -nargs 1 -- "C:\Program Files (x86)\IrfanView\i_view32.exe" @@
-target_offset: 指定被测函数在模块中的偏移

参考
https://www.apriorit.com/dev-blog/644-reverse-vulnerabilities-software-no-code-dynamic-fuzzinghttps://www.gosecure.net/blog/2019/07/30/fuzzing-closed-source-pdf-viewershttp://hdwsec.fr/blog/20161208-foxit/
☆?END?☆
OSRC 2周年第二弹——第五次奖励升级(不点后悔!!!)

关注公众号:拾黑(shiheibook)了解更多
[广告]赞助链接:
四季很好,只要有你,文娱排行榜:https://www.yaopaiming.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注网络尖刀微信公众号
关注网络尖刀微信公众号随时掌握互联网精彩
赞助链接
排名
热点
搜索指数
- 1 中共中央召开党外人士座谈会 7904359
- 2 日本附近海域发生7.5级地震 7809006
- 3 日本发布警报:预计将出现最高3米海啸 7713391
- 4 全国首艘氢电拖轮作业亮点多 7619587
- 5 课本上明太祖画像换了 7521211
- 6 中国游客遇日本地震:连滚带爬躲厕所 7425125
- 7 亚洲最大“清道夫”落户中国洋浦港 7328505
- 8 日本地震当地居民拍下自家书柜倒塌 7231737
- 9 熊猫宝宝聚餐横七竖八躺成一片 7141065
- 10 “人造太阳”何以照进现实 7048418







 OPPO安全应急响应中心
OPPO安全应急响应中心







