协议Fuzz技术

概述
https://sourceforge.net/projects/bacnetserver/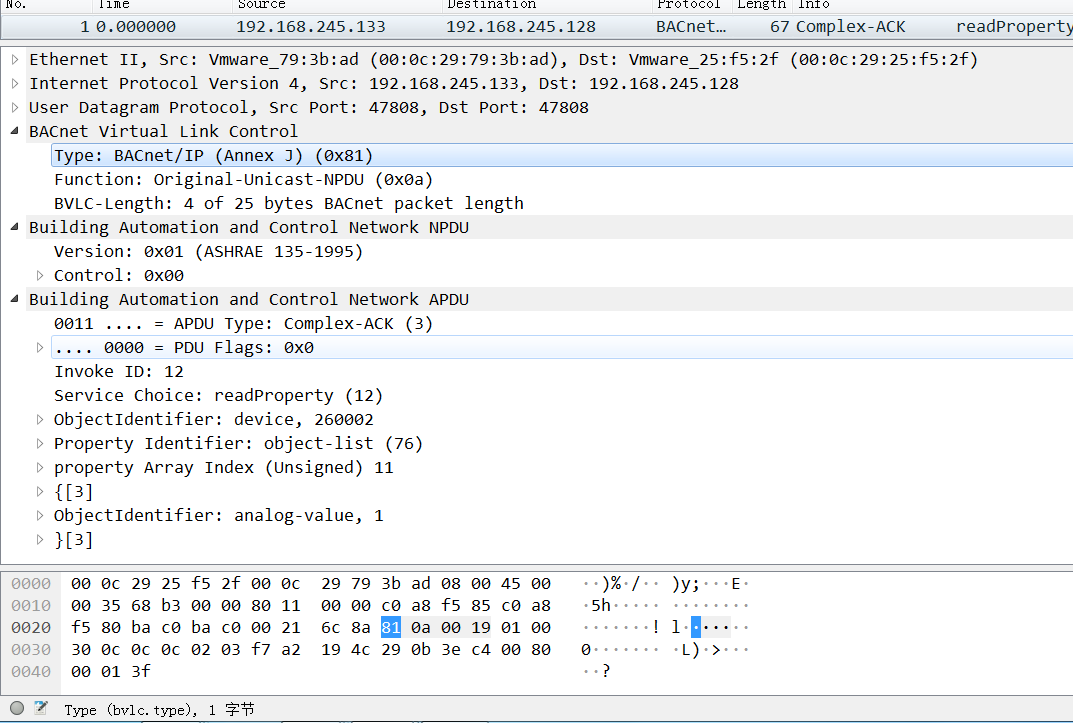
s_initialize("bacnet_packet")if s_block_start("block"):s_byte(0x81, name='type')s_byte(0x0a, name='function')s_word(0x19, name='bvlc-length', endian=BIG_ENDIAN)s_byte(0x01, name="version")s_byte(0x00, name="control")s_byte(0x30, name="type_flag")s_byte(0x03, name="id")s_byte(0xc, name="sc")s_byte(0xc, name="tag")s_dword(0x0203f7a2, name="type_number", endian=BIG_ENDIAN)s_byte(0x19, name="CT")s_byte(0x4c, name="PI")s_word(0x290b, name="PAI", endian=BIG_ENDIAN)s_byte(0x3e)s_byte(0xc4)s_dword(0x00800001, endian=BIG_ENDIAN)s_byte(0x3f)s_block_end()
session = Session()# 创建目标target = Target(connection=SocketConnection(target_ip, 47808, proto='udp'))target.procmon = boofuzz.instrumentation.External(pre=None, post=target_alive, start=reset_target, stop=None)session.add_target(target)s_initialize("bacnet_packet").........................................................session.connect(s_get("bacnet_packet"))session.fuzz()
def target_alive():try:client = socket.socket(type=socket.SOCK_DGRAM)decode_hex = codecs.getdecoder("hex_codec")send_data = decode_hex("810a001301040005010c0c0203f7a2194c2900")[0]client.sendto(send_data, (target_ip, 47808))client.settimeout(3.0)recv_data, address = client.recvfrom(1024)client.settimeout(None)client.close()if len(recv_data) > 0:return Trueelse:return Falseexcept:return False

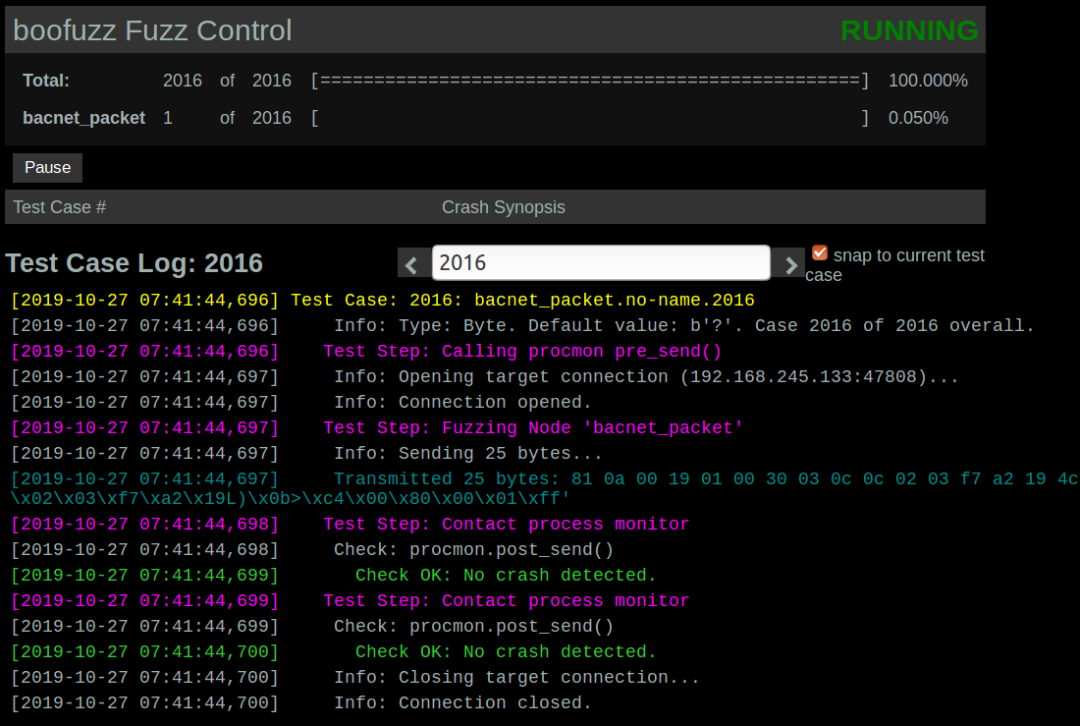
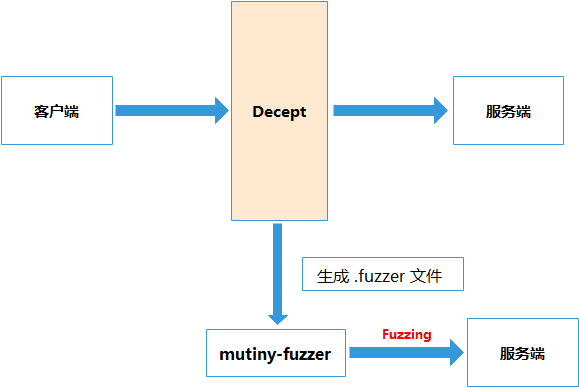
python decept.py 127.0.0.1 12245 192.168.245.133 47808 -l udp# 192.168.245.133为 Bacnet Server的IP地址
import socketimport codecstarget_ip = "127.0.0.1"port = 12245def main():client = socket.socket(type=socket.SOCK_DGRAM)decode_hex = codecs.getdecoder("hex_codec")send_data = decode_hex("810a001301040005010c0c0203f7a2194c2900")[0]client.sendto(send_data, (target_ip, port))client.settimeout(10.0)recv_data, address = client.recvfrom(1024)client.settimeout(None)client.close()print(recv_data.hex())if len(recv_data) > 0:return Trueelse:return Falseif __name__ == "__main__":main()
~/workplace/Decept$ python decept.py 127.0.0.1 12245 192.168.245.133 47808 -l udp -r udp --fuzzer bacnet.fuzzer[<_<] Decept proxy/sniffer [>_>][*.*] Listening on 127.0.0.1:12245[$.$] local:udp|remote:udp0000 81 0a 00 13 01 04 00 05 01 0c 0c 02 03 f7 a2 19 ................0010 4c 29 00 L).[o.o] 07:57:48.730920 Sent 19 bytes to remote (192.168.245.133:47808)0000 81 0a 00 16 01 00 30 01 0c 0c 02 03 f7 a2 19 4c ......0........L0010 29 00 3e 21 38 3f ).>!8?[o.o] 07:57:50.735225 Sent 22 bytes to local from 192.168.245.133:47808^CFile bacnet.fuzzer already exists, using bacnet.fuzzer-1 instead[^.^] Thanks for using Decept!
# Directory containing any custom exception/message/monitor processors# This should be either an absolute path or relative to the .fuzzer file# If set to "default", Mutiny will use any processors in the same# folder as the .fuzzer fileprocessor_dir default# Number of times to retry a test case causing a crashfailureThreshold 3# How long to wait between retrying test cases causing a crashfailureTimeout 5# How long for recv() to block when waiting on data from serverreceiveTimeout 1.0# Whether to perform an unfuzzed test run before fuzzingshouldPerformTestRun 1# Protocol (udp or tcp)proto udp# Port number to connect toport 47808# Port number to connect fromsourcePort -1# Source IP to connect fromsourceIP 0.0.0.0# The actual messages in the conversation# Each contains a message to be sent to or from the server, printably-formattedoutbound fuzz '\x81\n\x00\x13\x01\x04\x00\x05\x01\x0c\x0c\x02\x03\xf7\xa2\x19L)\x00'inbound '\x81\n\x00\x16\x01\x000\x01\x0c\x0c\x02\x03\xf7\xa2\x19L)\x00>!8?'
python mutiny.py bacnet.fuzzer 192.168.245.133# 192.168.245.133为 Bacnet Server的IP地址
import socketdef target_alive():try:client = socket.socket(type=socket.SOCK_DGRAM)send_data = "\x81\x04#\x00\x01\x13\n\x00\xe2\xf3\xef\xbb\xbf\xaf\x81\xa6\x05\x01\x0c)\x00\x02\x19\x03L\xa2"client.sendto(send_data,('192.168.46.128',47808))client.settimeout(10.0)re_Data,address = client.recvfrom(1024)client.settimeout(None)print(re_Data.encode('hex'))client.close()if len(re_Data) > 0:return Trueelse:return Falseexcept:return Falseprint target_alive()

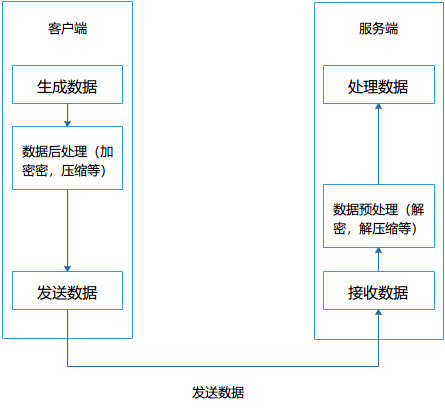
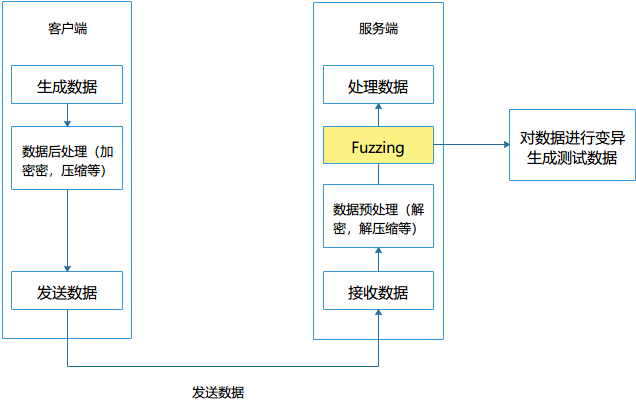
客户端会生成协议数据,然后可能会对数据进行加密,压缩等后处理操作,最后把数据通过网络发送到服务端。 服务端接收到数据,然后对数据进行预处理比如数据解密、解压缩等,最后对数据进行具体的处理。
.text:00432D1E push edx ; len.text:00432D1F mov eax, [ebp+buf].text:00432D22 push eax ; buf.text:00432D23 call sub_41B415.text:00432D28 push eax ; s.text:00432D29 call ds:recvfrom.text:00432D2F cmp esi, esp.text:00432D31 call j___RTC_CheckEsp.text:00432D36 mov [ebp+recvlen], eax.text:00432D3C jmp short loc_432D45
v36 = sub_41B415(v5);if ( select(v36 + 1, &readfds, 0, 0, &timeout) <= 0 )return 0;s = sub_41B415(&from);recvlen = recvfrom(s, buf, len, 0, &from, &fromlen); // 读取 udp 数据if ( recvlen < 0 )return 0;if ( !recvlen )return 0;if ( *buf != 129 )return 0;byte_from_buf = buf[1]; // 从读取的buf中取出一个字节extract_word_from_buf((buf + 2), &word_from_buf); // 从 buf 里面取出2个字节word_from_buf -= 4;v16 = byte_from_buf;switch ( byte_from_buf ) // 根据 byte_from_buf 决定后续的数据的处理{case 0:extract_word_from_buf((buf + 4), &v21);dword_4D8648 = v21;sub_433740("BVLC: Result Code=%d\n");word_from_buf = 0;break;case 1:sub_433740("BVLC: Received Write-BDT.\n");v19 = sub_433960(buf + 4, word_from_buf);..........................................................................................
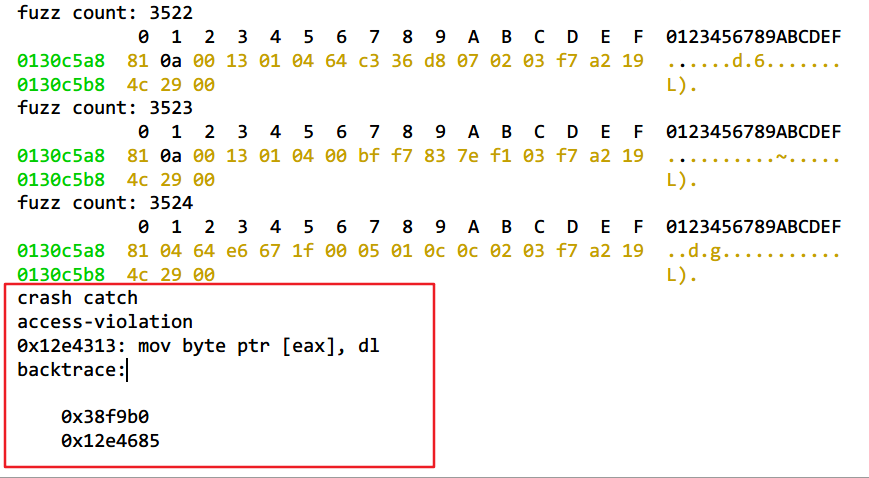
//设置异常Process.setExceptionHandler(function (details) {if (details.type != "system") {console.log(details.context);console.log(details.type);console.log(details.address);console.log(details.memory);var backtrace = Thread.backtrace(details.context, Backtracer.ACCURATE).map(DebugSymbol.fromAddress).join('\\n\\t');console.log(backtrace);}return false;});//生成从minNum到maxNum的随机数function generate_random_number(minNum, maxNum) {switch (arguments.length) {case 1:return parseInt(Math.random() * minNum + 1, 10);break;case 2:return parseInt(Math.random() * (maxNum - minNum + 1) + minNum, 10);break;default:return 0;break;}}var fuzz_count = 1;function fuzz(buf, size) {var fuzz_size = parseInt(size * 0.3, 10);console.log("fuzz size: " + fuzz_size);var offset = generate_random_number(0, size - fuzz_size - 1);for (var i = 0; i < fuzz_size; i++) {buf.add(offset + i).writeU8(generate_random_number(0, 255));}console.log("fuzz count: " + fuzz_count);fuzz_count += 1;console.log(hexdump(buf, {offset: 0,length: size,header: true,ansi: true}));}var recv_from = Module.findExportByName(null, "recvfrom");Interceptor.attach(recv_from, {onEnter: function (args) {// console.log("socket: " + args[0]);// console.log("buffer: " + args[1]);this.buffer = args[1];},onLeave: function (retval) {// console.log("recvfrom length: " + retval);fuzz(this.buffer, retval.toInt32());}});
function (args) {this.buffer = args[1];}
function (retval) {fuzz(this.buffer, retval.toInt32());}
function fuzz(buf, size) {var fuzz_size = parseInt(size * 0.3, 10);console.log("fuzz size: " + fuzz_size);var offset = generate_random_number(0, size - fuzz_size - 1);for (var i = 0; i < fuzz_size; i++) {buf.add(offset + i).writeU8(generate_random_number(0, 255));}console.log(hexdump(buf, {offset: 0,length: size,header: true,ansi: true}));}
def send_loop():import timeclient = socket.socket(type=socket.SOCK_DGRAM)decode_hex = codecs.getdecoder("hex_codec")send_data = decode_hex("810a001301040005010c0c0203f7a2194c2900")[0]while True:client.sendto(send_data, (target_ip, port))time.sleep(0.1)client.close()
☆ END ☆
OSRC 2周年第二弹——第五次奖励升级(不点后悔!!!)

关注公众号:拾黑(shiheibook)了解更多
[广告]赞助链接:
四季很好,只要有你,文娱排行榜:https://www.yaopaiming.com/
让资讯触达的更精准有趣:https://www.0xu.cn/
 关注网络尖刀微信公众号
关注网络尖刀微信公众号随时掌握互联网精彩
赞助链接
排名
热点
搜索指数
- 1 中法元首相会都江堰 7904619
- 2 中方不接受日方所谓交涉 已当场驳回 7809318
- 3 大闸蟹为何会在欧美泛滥成灾 7714632
- 4 国际机构看中国经济 关键词亮了 7616087
- 5 家长称婴儿被褥印不雅英文单词 7524087
- 6 日方军机滋扰擅闯或被视为训练靶标 7428763
- 7 罪犯被判死缓破口大骂被害人一家 7329790
- 8 国乒8比1击败日本队 11战全胜夺冠 7232598
- 9 长沙一男子要取现20万 银行紧急报警 7136430
- 10 千吨级“巨无霸”就位 7048350







 OPPO安全应急响应中心
OPPO安全应急响应中心







